- What Is Endpoint Detection and Response (EDR) Deployment?
- What is EDR-as-a-Service Managed Security?
- What Are Endpoint Detection and Response Tools?
- What is EDR vs. Antivirus?
- How Does EDR Enhance Small Business Cybersecurity?
- How Does EDR Leverage Machine Learning?
-
What Is Endpoint Detection and Response (EDR) Management?
- EDR Management Explained
- Key Capabilities of EDR Management
- The Crucial Role of EDR Management in Modern Cybersecurity
- EDR Management Challenges and Solutions
- Best Practices for Effective EDR Management
- EDR vs. EPP: A Complementary Relationship
- Integrating EDR Management with a Broader Security Ecosystem
- Case Study of a Successful EDR Implementation
- EDR Management FAQs
- What Is Endpoint Detection and Response (EDR) Compliance?
- What is the Difference Between EDR vs. SIEM?
- What is EDR vs. XDR?
What Is Endpoint Detection and Response (EDR)?
EDR (Endpoint Detection and Response) is a cybersecurity solution that continuously monitors and records endpoint activity, such as laptops, desktops, servers, and mobile devices. It provides real-time visibility into threats, enabling rapid detection, investigation, and automated response capabilities to neutralize malicious activities before they compromise an organization's systems.
Key Points
-
EDR continuously monitors endpoint activity, offering real-time visibility for rapid threat detection, investigation, and automated response. -
EDR solutions identify unusual behaviors and sophisticated attack patterns, including IoCs and TTPs linked to advanced threats. -
Successful EDR implementation needs careful planning, effective deployment, and continuous configuration to optimize performance and reduce false positives. -
Advanced EDR strategies encompass proactive threat hunting, SOAR/SIEM integration, and the utilization of AI/ML for enhanced detection and response. -
EDR provides deeper visibility, behavioral analytics, and comprehensive incident response, distinguishing it from traditional AV and EPP, while complementing SIEM with granular endpoint data.
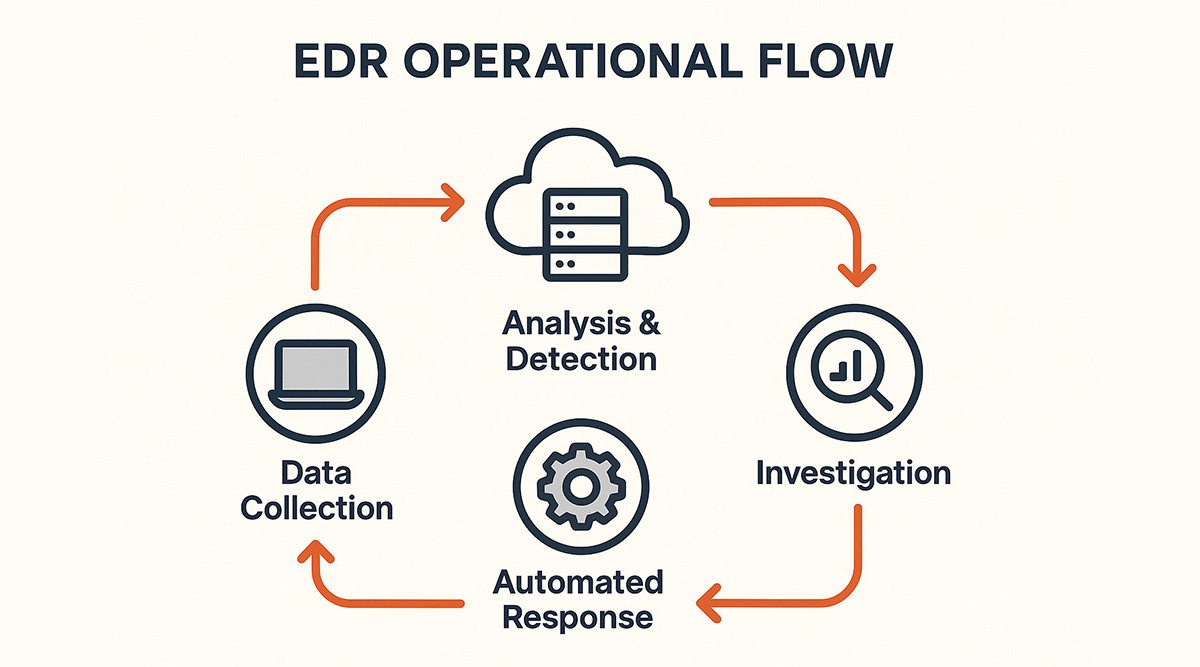
Figure 1: The typical operational flow of an EDR system
Understanding EDR
EDR solutions offer a proactive defense against evolving threats. They collect and analyze telemetry data from endpoints, including:
- Process execution
- File system changes
- Network connections
- User activities
This continuous monitoring enables security teams to identify anomalous behaviors that may indicate a sophisticated attack, even those evading traditional signature-based defenses.
The significance of EDR stems from its ability to provide deep visibility into what is happening at the endpoint level, which is often the initial point of compromise for many cyber attacks. By correlating events and applying behavioral analytics, EDR can detect subtle indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with advanced persistent threats (APTs) and zero-day exploits.
This comprehensive approach empowers security professionals to understand the full scope of an attack, contain it swiftly, and effectively remediate its impact, thereby minimizing potential damage and downtime.
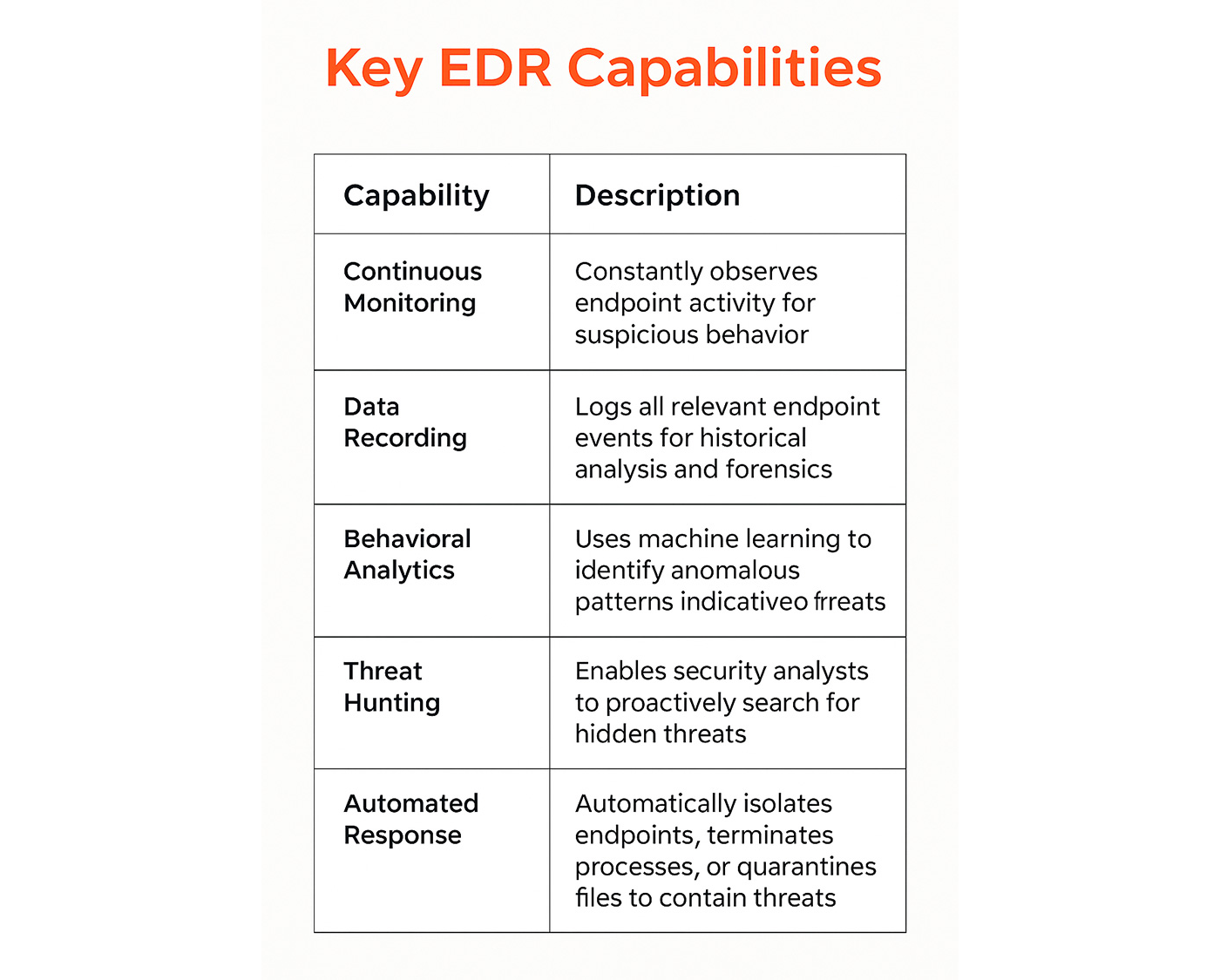
Figure 2: Essential capabilities of EDR solutions
Key Benefits of EDR Solutions
EDR solutions provide significant advantages for enterprises looking to enhance their cybersecurity posture:
- Granular visibility into endpoint activities helps security teams detect and respond to threats more efficiently than traditional security tools.
- Quickly identifying and containing threats minimizes potential damage and reduces recovery time.
- Automated response capabilities within EDR platforms reduce the manual effort required for remediation, allowing security analysts to focus on more complex investigations.
- Supports proactive threat hunting, enabling organizations to identify and address hidden threats before they escalate into major incidents.
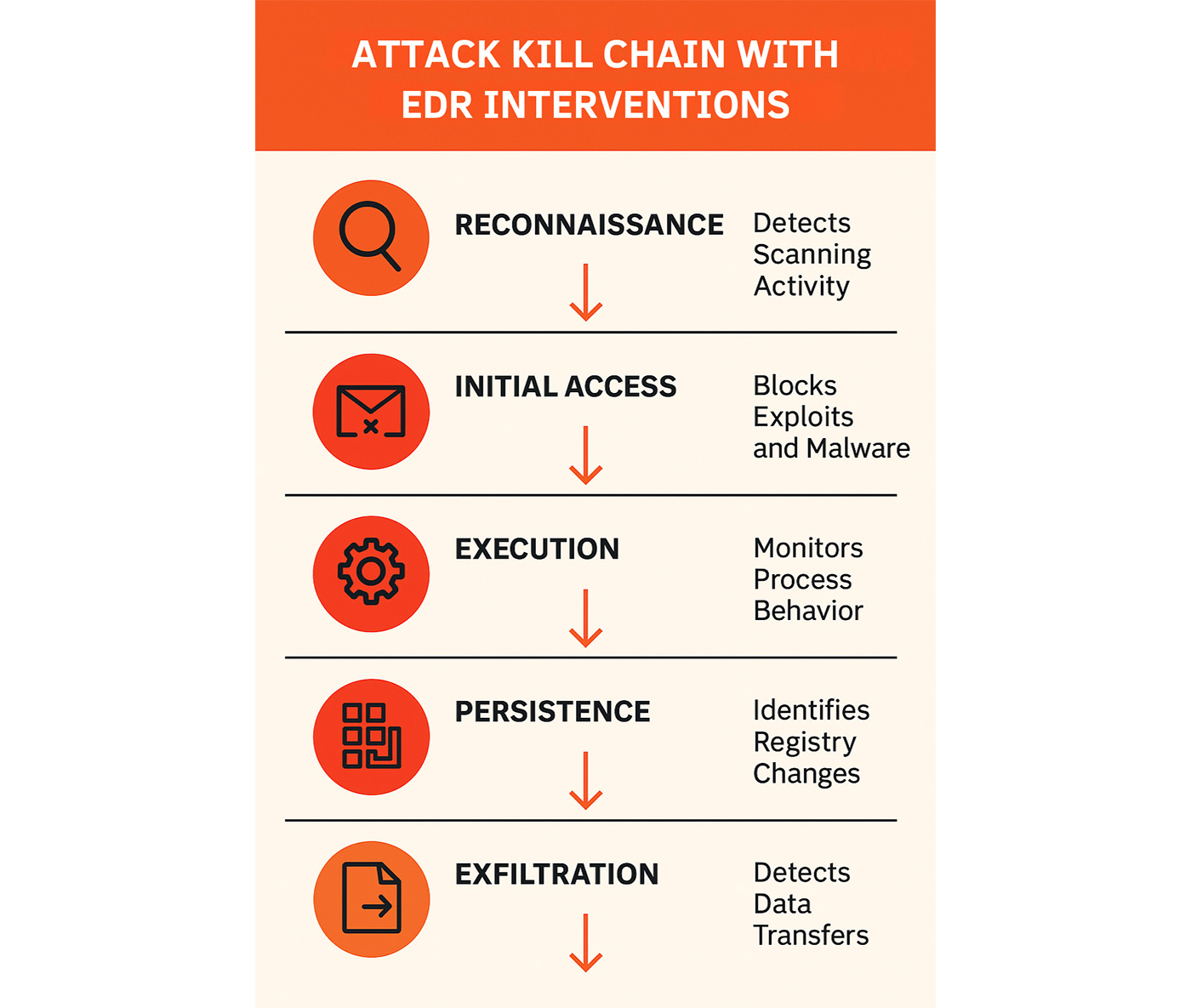
Figure 3: EDR tools intervene at various stages of a cyberattack kill chain
How EDR Works: A Detailed Breakdown
EDR platforms operate by continuously monitoring endpoints and collecting vast amounts of data to detect and respond to threats. This intricate process involves several key stages, from data collection to automated response. Understanding these mechanisms is crucial for leveraging EDR effectively in a modern security environment.
Data Collection and Telemetry
EDR agents deployed on endpoints continuously gather telemetry data. This data includes process activity, file modifications, network connections, registry changes, and user actions. The rich dataset provides a comprehensive picture of endpoint behavior.
This information is then sent to a centralized EDR platform for analysis. The sheer volume of data necessitates efficient collection and storage mechanisms to ensure real-time processing and historical lookup capabilities.
Behavioral Analytics and Threat Detection
Once collected, the telemetry data undergoes sophisticated analysis using behavioral analytics, machine learning, and rule-based detection engines. These techniques help identify anomalies and patterns indicative of malicious activity.
For example, an executable running from an unusual location or attempting to modify critical system files would trigger an alert. The system correlates events across multiple endpoints and over time, building a contextual understanding of potential threats. This helps in detecting sophisticated threats, such as zero-day exploits and advanced persistent threats.
Investigation and Forensics
When a suspicious activity is detected, EDR provides security analysts with the tools to investigate further. Analysts can drill down into specific events, view the chain of execution, and understand the scope and impact of an alert.
This capability facilitates forensic analysis, enabling teams to determine the root cause of an incident and identify compromised systems. EDR platforms often include capabilities to reconstruct attack timelines, aiding in thorough post-incident review.
Automated Response Capabilities
EDR solutions integrate automated response actions to swiftly contain threats. These actions can include:
- Isolating a compromised endpoint from the network
- Terminating malicious processes
- Quarantining suspicious files
Automation helps reduce the dwell time of threats and prevents lateral movement within the network, minimizing the attack surface. While automation is powerful, human oversight remains crucial to ensure timely and appropriate responses and prevent disruptions to legitimate business operations.
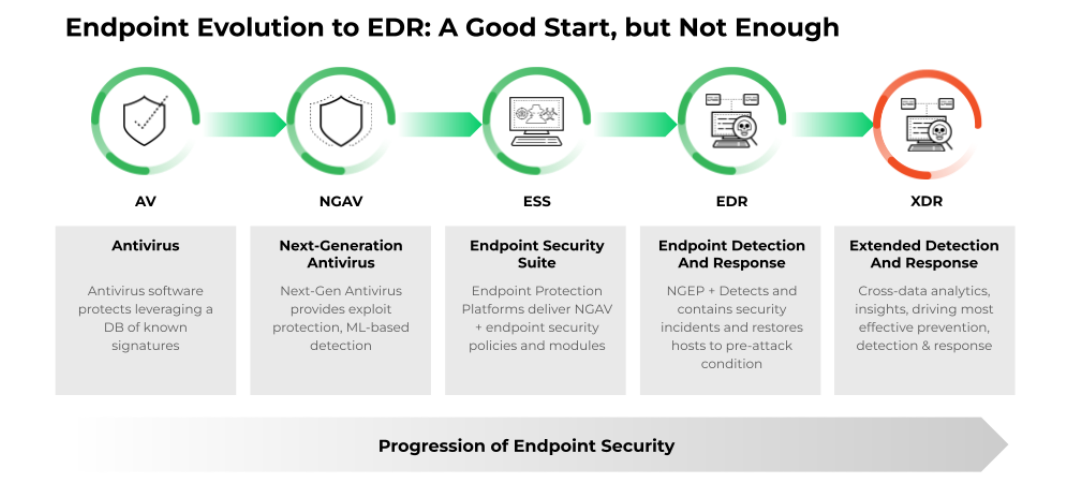
Figure 4: The evolution of endpoint security from simple antivirus to comprehensive extended detection and response solutions.
Evolution of EDR
EDR emerged from the limitations of traditional antivirus solutions, which primarily focused on known threats.
2010
The concept gained traction in the early 2010s as cyber threats became more sophisticated and elusive. Early EDR tools provided basic monitoring and alerting capabilities, but they quickly evolved to include advanced analytics and machine learning.
2013
By 2013, EDR solutions began incorporating behavioral analysis to detect anomalies and potential threats in real time. This marked a significant shift from signature-based detection to a more proactive approach. The integration of threat intelligence feeds further enhanced EDR's capabilities, allowing for the identification of emerging threats before they can cause significant harm.
As cyber attacks grew in complexity, EDR systems adapted by offering automated response features. These advancements enabled security teams to detect and swiftly mitigate threats, reducing the attacker’s window of opportunity. Today, EDR stands as a cornerstone of modern cybersecurity strategies.
EDR Implementation Process
Deploying an EDR solution effectively requires careful planning and execution to integrate it seamlessly into an existing security infrastructure. A structured approach ensures maximum benefit and minimizes potential disruptions. From initial preparation to ongoing configuration, each step plays a vital role in optimizing EDR performance.
Planning and Preparation
Before deploying EDR, organizations must:
- Define their security objectives
- Assess their current endpoint landscape
- Identify all endpoints and understand their operating systems
- Determine network architecture
A clear understanding of these factors helps in selecting the right EDR solution and preparing the environment for agent deployment. Establishing clear roles and responsibilities for the security team is also crucial.
Deployment Strategies
EDR agents can be deployed using various methods, including group policy, software deployment tools, or manual installation. The chosen strategy depends on the organization's size, infrastructure, and existing management tools.
A phased rollout is often recommended to monitor performance and address any issues before a full-scale deployment. Ensuring agents are installed correctly and communicate effectively with the central EDR platform is paramount.
Configuration and Tuning
After deployment, configuring and tuning the EDR solution is essential to optimize its performance and minimize false positives. This involves setting up detection rules, defining response actions, and integrating with other security tools, such as SIEMs.
Continuous monitoring of alerts and fine-tuning policies based on observed threats helps refine the EDR's accuracy. Regular reviews of security policies ensure they align with evolving threat landscapes and organizational needs.
Common Challenges and Solutions in EDR Adoption
Implementing an EDR solution, while beneficial, can present several challenges for organizations. Addressing these common hurdles proactively ensures a smoother adoption process and maximizes the return on investment. From managing alert volumes to integrating with existing systems, understanding these obstacles and their solutions is key to successful EDR deployment.
Alert Fatigue
One of the most significant challenges in EDR adoption is alert fatigue, where security analysts are overwhelmed by the sheer volume of alerts generated by the system. Many of these alerts might be benign or low-priority, leading to missed critical threats.
To combat this, organizations should fine-tune their EDR policies, prioritize alerts based on severity and context, and leverage automation to handle low-fidelity events. Integrating EDR with a Security Information and Event Management (SIEM) system can help correlate alerts and reduce noise.
Integration Complexities
Integrating EDR with existing security tools, such as firewalls, intrusion detection systems, and identity management solutions, can be a complex process. Incompatible APIs, data format discrepancies, and a lack of standardized communication protocols often hinder seamless integration.
Addressing this requires choosing EDR solutions with open APIs and resilient integration capabilities. Custom scripting or middleware might be necessary to bridge gaps between disparate systems.
Resource Constraints
Implementing and managing an EDR solution demands skilled personnel and significant resources. Many organizations, especially smaller ones, struggle with a shortage of cybersecurity experts capable of operating and optimizing EDR platforms.
Outsourcing EDR management to a Managed Detection and Response (MDR) provider can alleviate resource constraints. Additionally, investing in training for internal teams ensures they possess the necessary skills to leverage the EDR effectively.
Advanced EDR Strategies and Optimization Techniques
Moving beyond basic EDR deployment, organizations can adopt advanced strategies to maximize their investment and enhance their threat detection and response capabilities. These techniques leverage the full potential of EDR to provide deeper insights and proactive security measures.
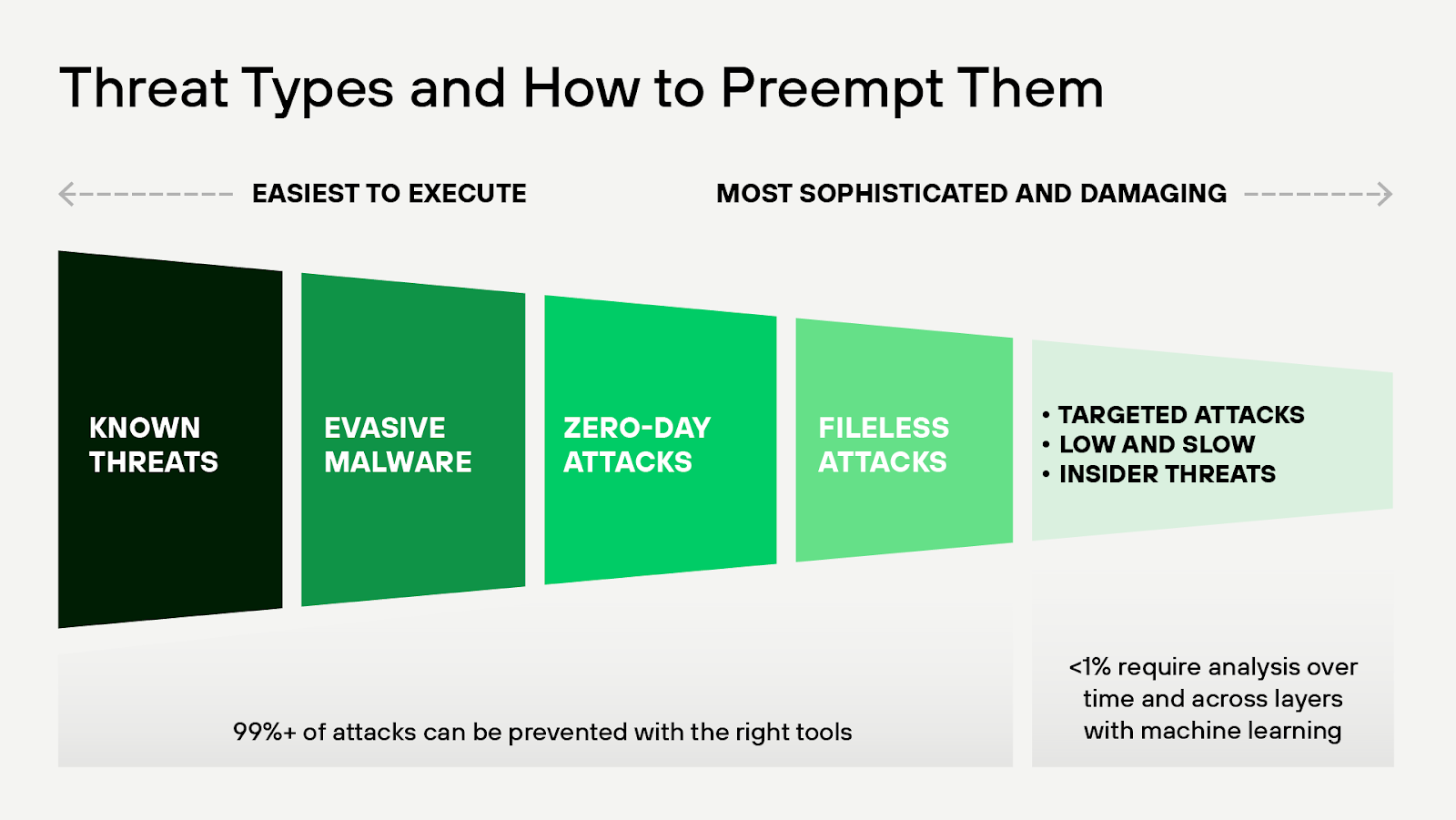
Figure 5: Most attacks can be prevented with the right tools. Less than 1% of targeted attacks require analysis over time and across layers with ML.
Proactive Threat Hunting
While EDR excels at automated detection, proactive threat hunting enables security teams to search for undetected threats within their environment actively. This involves leveraging EDR data to identify suspicious patterns, anomalies, or indicators of compromise that may have bypassed automated defenses.
Threat hunters hypothesize potential attack scenarios and use EDR's investigative capabilities to validate or refute them. This human-driven approach uncovers sophisticated, stealthy attacks that automated systems might miss.
Integration with SOAR and SIEM
Integrating EDR with Security Orchestration, Automation, and Response (SOAR) platforms and Security Information and Event Management (SIEM) systems creates a powerful, unified security ecosystem.
SIEM aggregates logs and alerts from various sources, providing a centralized view of security events. SOAR automates repetitive tasks and orchestrates complex incident response workflows.
This integration enables the automated enrichment of EDR alerts with contextual data from SIEM and triggers automated response actions by SOAR based on EDR detections, streamlining the entire incident lifecycle.
Leveraging AI and Machine Learning in EDR
Artificial intelligence (AI) and machine learning (ML) are becoming increasingly vital in optimizing EDR effectiveness. AI/ML algorithms can analyze vast datasets of endpoint telemetry to identify subtle patterns of malicious behavior that human analysts or rule-based systems might overlook.
This includes detecting polymorphic malware, fileless attacks, and sophisticated social engineering attempts. Leveraging AI/ML enhances detection accuracy, reduces false positives, and continuously adapts to new threats, thereby improving the EDR's ability to stay ahead of adversaries.
EDR and the Evolving Threat Landscape
The cybersecurity threat landscape constantly evolves, with adversaries employing increasingly sophisticated tactics. EDR plays a pivotal role in countering these emerging threats and adapts to new challenges. The impact of artificial intelligence further reshapes how incidents are responded to and reported.
Emerging Threats and EDR's Role
As cybercriminals adopt advanced techniques, traditional signature-based security solutions often prove inadequate. EDR's behavioral analysis capabilities are critical for detecting these emerging threats.
By monitoring process execution, network connections, and system calls for unusual patterns, EDR can identify malicious activity even when no known signature exists. Its continuous monitoring and forensic capabilities also help in understanding the scope and impact of novel attacks, aiding in rapid containment and remediation.
Impact of AI on Incident Response and Reporting
Artificial intelligence has a significant impact on incident response and reporting processes. AI-powered EDR solutions can automatically analyze vast amounts of data, identifying anomalies and prioritizing alerts with greater accuracy and speed than human analysts alone. This accelerates threat detection and reduces response times.
AI also assists in automating routine tasks, such as initial alert triage and data enrichment, freeing up security teams to focus on complex investigations.
Furthermore, AI can aid in generating more comprehensive and insightful incident reports by correlating disparate data points and highlighting critical attack details, improving post-incident analysis and future prevention strategies.
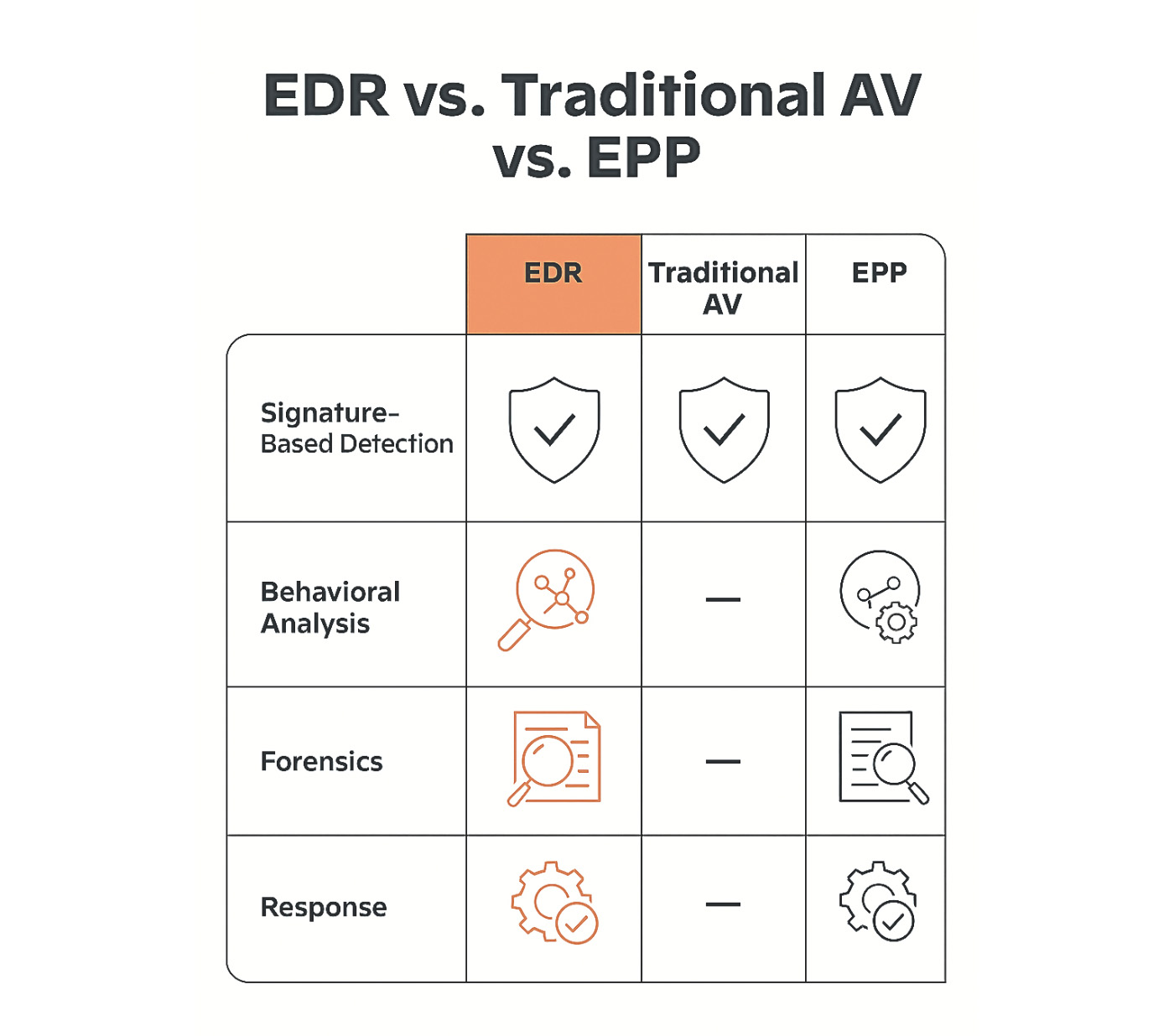
Figure 6: EDR vs Traditional AV vs. EPP
Comparison of EDR with Other Security Solutions
Understanding how EDR complements or differs from other common security solutions is crucial for building a layered defense strategy. While some functionalities may overlap, each technology addresses specific aspects of endpoint security. A comprehensive approach often involves integrating these solutions for maximum protection.
EDR vs. Antivirus (AV)
Traditional antivirus (AV) primarily focuses on preventing known malware infections by using signature-based detection and heuristic analysis. It excels at blocking common viruses, worms, and Trojans.
EDR, conversely, goes beyond prevention by continuously monitoring endpoint activity and detecting more sophisticated, unknown threats that might bypass AV. EDR provides visibility into post-compromise activity, allowing for detection, investigation, and response to active attacks, whereas AV often stops at blocking initial infection attemts.
EDR vs. Endpoint Protection Platforms (EPP)
Endpoint Protection Platforms (EPP) represent a broader suit of security controls, often including antivirus, firewall, device control, and sometimes basic EDR capabilities. EPP aims to prevent a wide range of threats.
While EPP offers a foundational layer of protection, EDR provides deeper visibility, advanced behavioral analytics, and more granular investigative and response capabilities. EDR is designed to detect and respond to advanced threats, such as fileless attacks or insider threats, that may evade the preventative measures of an EPP. EPP focuses on preventing incidents, while EDR focuses on detecting and responding to those that slip through.
EDR vs. SIEM
SIEM systems aggregate and analyze log data from various security devices and applications across an entire IT infrastructure. SIEM provides a centralized view of security events, helping with compliance reporting and broad threat correlation.
EDR, however, specializes in deep, granular visibility and activity monitoring at the endpoint level. While SIEM collects logs from EDR, EDR itself provides the detailed forensic data and immediate response capabilities for endpoint-specific incidents. SIEM provides a broad view, while EDR offers a thorough examination of endpoint activities.
EDR and Small Business Cybersecurity
EDR enhances small business cybersecurity by providing automated, proactive, and comprehensive protection against cyber threats, ensuring business continuity and regulatory compliance.
Small businesses can benefit from EDR in the following ways:
- Proactive Threat Detection: EDR continuously monitors endpoints (like laptops, smartphones, or servers) for suspicious activity, detecting potential threats before they can cause significant damage.
- Rapid Incident Response: When EDR detects a threat, it can automatically isolate the compromised device, preventing the attack from spreading to other network parts.
- Comprehensive Visibility: EDR solutions provide visibility into all devices and activities within a network, helping small businesses track user behavior, identify vulnerabilities, and understand the scope of threats, making it easier to prevent future attacks.
- Automated Threat Remediation: EDR tools often have automation capabilities that enable them to detect threats and automatically respond to and neutralize them, reducing the burden on small business IT staff.
- Data Protection and Compliance: EDR helps small businesses comply with data protection regulations by ensuring that sensitive data remains secure. It also provides detailed logs and reports that can be used for audits and compliance verification.
- Cost Efficiency: For small businesses, EDR's affordability compared to the potential cost of a cyber breach makes it an effective and budget-friendly cybersecurity solution.
How to Evaluate an EDR Solution
Selecting the right EDR solution fortifies your organization's security posture, safeguarding sensitive data and ensuring operational continuity. However, the evaluation process can seem daunting with a myriad of EDR solutions available on the market.
The goal is to make an informed decision that best aligns with an organization's needs and security requirements.
By understanding what to look for in terms of features, performance, integration capabilities, and support, you can select an EDR solution that meets compliance standards and enhances your incident response strategies and overall cybersecurity resilience.
Broad Visibility and ML-based Attack Detection
Rich data is the foundation for EDR. Look for endpoint detection and response tools that collect comprehensive data and provide enterprise-wide visibility. Ideal solutions offer extensive machine learning and analytics techniques to detect advanced threats in real-time. Consider independent tests, such as the MITRE ATT&CK Evaluation, to assess the breadth and accuracy of detection coverage.
Simplified Investigations
Select security tools that offer a comprehensive view of incidents, including detailed investigative information, to minimize response times. They should simplify investigations by automatically revealing the root cause, sequence of events, and threat intelligence details of alerts from any source.
Customizable incident scoring allows you to focus on the events that matter most. By grouping alerts into security incidents, you can reduce the number of individual events to investigate by 98%, speeding incident response.
Coordinated Response Across Enforcement Points
Flexible response options, including script execution, direct access to endpoints, host restore, and “search and destroy,” enable you to eliminate threats and recover from attacks quickly.
Tight integration with security orchestration, automation, and response (SOAR) tools enables you to automate playbooks and extend responses to hundreds of security and IT tools. EDR solutions can even restore damaged files and registry settings if ransomware encrypts endpoint data.
Ironclad Endpoint Threat Prevention
The best EDR security includes antivirus and endpoint security capabilities to block every stage of an attack. Evaluate whether endpoint security solutions can block exploits by technique, block malware files using machine learning, and stop malicious behavior.
With effective endpoint threat prevention, you can shut down the most evasive attacks.
Endpoint Protection Suite Capabilities to Reduce Attack Surface
Ideally, EDR tools should block attacks and ransomware, preventing data loss and unauthorized access with features such as host firewall, device control, and disk encryption. Look for an EDR tool that provides granular control over USB access and firewall policies.
A Single, Lightweight Agent
Instead of installing bulky agents that continually scan your endpoints for attack signatures, opt for one end-to-end agent for endpoint threat prevention and EDR.
Cloud-Delivered Security
Cloud-based management and deployment streamline operations and eliminate burdensome on-premises servers. They also quickly scale to handle more users and data.
Optional Managed Services
EDR solutions should offer managed threat hunting and MDR to provide 24x7 monitoring, threat hunting, and triage. MDR services can be provided through managed detection and response partners.
