-
What Is Endpoint Security? EPP, EDR, and XDR Explained
- Key Data: Fronts of Attacks
- Why Endpoint Security Is Mandatory
- How Does Endpoint Security Work?
- Types of Endpoint Security: A Multi-Layered Approach
- Traditional Antivirus vs. Modern Endpoint Security
- Implementing Zero Trust for Endpoint Security
- Other Key Components
- Selecting the Optimal Endpoint Security Solution
- Strategic Endpoint Security: Challenges and Best Practices
- Endpoint Security FAQs
- What Is the Difference Between Advanced Endpoint Security and Antivirus (AV)?
-
What is Endpoint Security Awareness Training?
- Understanding Security Awareness Training
- Endpoint Security Awareness Training Explained
- What Does Endpoint Security Awareness Training Cover?
- Why Is Security Awareness Training Important?
- How to Build an Effective Endpoint Security Awareness Training Program
- Industry Awareness Training Case Studies and Success Stories
- The Future of Endpoint Security Awareness Training
- Endpoint Security Awareness Training FAQs
- What Is Endpoint Detection?
-
What Is Endpoint Security Software? How It Stops Cyberattacks
- Endpoint Security Software Explained
- Endpoint Security Software vs. Antivirus
- Core Components of Comprehensive Endpoint Security Software
- How Does Endpoint Security Software Protect a Network?
- What are the Key Features of Endpoint Security Software?
- EPP vs. EDR vs. XDR
- The Role of Threat Hunting in Endpoint Security
- Implementation Strategies for Enterprise Environments
- Defending Against Ransomware: A Use Case
- Endpoint Security Software FAQs
- What Is an Endpoint? Understand Devices, Risks & Security
- What are the Types of Endpoint Security?
- What Is Next-Generation Antivirus (NGAV)
-
What Is Endpoint Security Antivirus?
- Endpoint Security Antivirus Explained
- Understanding Endpoints in Cybersecurity
- Why Endpoint Security Antivirus is Crucial for Modern Cybersecurity
- Endpoint Antivirus vs. Endpoint Security: What Is the Difference?
- Key Components of a Comprehensive Endpoint Security Solution
- How Endpoint Security Antivirus Works
- Implementing and Optimizing Endpoint Security Antivirus
- Choosing the Right Endpoint Security Antivirus Solution
- Challenges and Future Trends in Endpoint Security
- Endpoint Security Antivirus FAQs
What Is an Endpoint Protection Platform?
An Endpoint Protection Platform (EPP) is a comprehensive, integrated security solution that combines multiple protection capabilities into a unified platform designed to prevent, detect, and respond to threats targeting endpoint devices.
Understanding Endpoint Protection Platforms (EPPs)
According to Gartner, an EPP is "a solution deployed on endpoint devices to prevent file-based malware attacks, detect malicious activity, and provide the investigation and remediation capabilities needed to respond to dynamic security incidents and alerts."
Here’s a breakdown of what that means:
- Endpoint Devices: These are the "end points" of a network, where users interact with data and applications. They are often the primary targets for cyberattacks.
- Prevention: EPPs aim to stop threats before they can execute or cause harm. This includes traditional methods like signature-based detection (matching known malware patterns) but increasingly relies on more advanced techniques.
- Detection: Even if a threat bypasses initial prevention, an EPP is designed to identify suspicious behavior or indicators of compromise (IoCs) that suggest a potential breach.
- Blocking/Remediation: Once a threat is detected, the EPP can take action to isolate, quarantine, or remove the malicious file or process, preventing it from spreading or causing further damage.
Modern EPPs integrate advanced technologies including next-generation antivirus, behavioral analysis, machine learning, threat intelligence, and automated response capabilities. Advanced EPP solutions use multiple detection techniques and are primarily cloud-managed and cloud-data-assisted, allowing continuous monitoring and collection of activity data with the ability to take remote remediation actions.
The Importance of Endpoint Protection for Enterprises
Today, enterprises face an ever-evolving threat landscape that requires comprehensive measures to protect sensitive data and maintain operational integrity. Endpoint protection platforms safeguard organizations from many cyber threats, including malware, ransomware, and unauthorized access attempts.
With the increasing prevalence of remote work and the proliferation of devices accessing corporate networks, the necessity for comprehensive endpoint security has never been greater. By investing in advanced endpoint protection, enterprises not only fortify their defenses against current threats but also position themselves to adapt to future security challenges and regulatory standards.
Furthermore, endpoint protection complements broader cybersecurity strategies, offering a solid foundation upon which enterprises can build additional layers of security, such as network firewalls and security awareness training.
The global endpoint protection platform market is projected to grow from $17.4 billion in 2024 to $29.0 billion by 2029, with a compound annual growth rate (CAGR) of 10.7%. This growth reflects the increasing sophistication of cyber threats and the critical need for comprehensive endpoint security.
According to recent data, 68% of organizations experience endpoint security attacks involving malware, stolen devices, or compromised credentials. The shift to remote and hybrid work models has exponentially increased the attack surface, making endpoint protection more crucial than ever.
What Cybersecurity Practitioners and CISOs Need to Know About EPPs
Endpoint Protection Platforms (EPPs) play a critical role in modern enterprise defense. Whether you're a security practitioner managing day-to-day operations or a CISO responsible for strategic risk mitigation, a clear understanding of EPP capabilities, operational requirements, and long-term value is essential.
For Cybersecurity Practitioners (Security Analysts, Engineers, SOC Teams):
As frontline defenders, practitioners must have deep, hands-on expertise with EPP technologies to ensure optimal protection, performance, and operational efficiency.
Understand Core Capabilities
Move beyond feature familiarity—gain a functional understanding of how EPP components work. How does next-generation antivirus (NGAV) use behavioral analytics, machine learning, and exploit prevention to stop zero-day threats? Explore all integrated modules—including host firewall, device control, application control, and web filtering—and learn how to configure each to maximize protection while minimizing user impact.
Optimize Deployment and Policy Management
Efficient deployment and tuning are critical. Master installation methods such as Group Policy Objects (GPO), System Center Configuration Manager (SCCM), and Mobile Device Management (MDM). Understand best practices for health monitoring, agent troubleshooting, and precise policy creation. Learn to manage inheritance and exceptions without introducing new risks.
Streamline Alert Management and Integration
Alert fidelity directly impacts operational efficiency. Evaluate the accuracy and contextual depth of alerts—are they enriched with process trees, user details, and network connections? Determine how seamlessly alerts integrate with your existing SIEM, SOAR, or ticketing systems to enhance response workflows.
Address Performance and User Impact
Performance concerns are common. Analyze the EPP agent’s resource consumption and its impact on CPU and memory usage. Leverage available diagnostic tools to identify and resolve conflicts or performance degradation caused by other software or system configurations.
For CISOs (Chief Information Security Officers):
CISOs must align endpoint protection initiatives with business risk, compliance mandates, and long-term security strategy. EPPs are not just technical controls—they are strategic investments in organizational resilience.
Evaluate Risk Reduction and Strategic Alignment
Assess how effectively the EPP reduces risk from high-impact threats such as ransomware, data exfiltration, and insider attacks. Determine how well it complements existing security controls—including identity, cloud, and network security—and supports regulatory compliance frameworks such as HIPAA, PCI DSS, and GDPR.
Validate Efficacy Through Independent Testing
Rely on objective third-party evaluations rather than vendor claims. Use resources such as MITRE ATT&CK evaluations, AV-Test results, and Gartner Magic Quadrants to evaluate detection capabilities, false positive rates, and performance under real-world attack scenarios. Assess how well the solution supports detection and response post-breach.
Analyze Total Cost of Ownership (TCO)
Go beyond licensing costs. Consider the administrative overhead, training requirements, and integration complexity. Poor tool interoperability often results in manual processes that consume valuable analyst time. Evaluate whether a cloud-native architecture offers greater flexibility and cost-efficiency for your distributed workforce.
Plan for EDR and XDR Evolution
Ensure the EPP is part of a broader roadmap that includes Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR). These capabilities are critical for enhancing threat visibility, accelerating investigations, and enabling proactive threat hunting.
Assess Vendor Viability and Support
Vendor strength is as important as product capability. Evaluate the vendor’s financial stability, pace of innovation, and support infrastructure, including 24/7 availability and service-level agreements (SLAs). Consider whether their roadmap aligns with your long-term security needs and whether they can serve as a trusted partner during high-impact incidents.
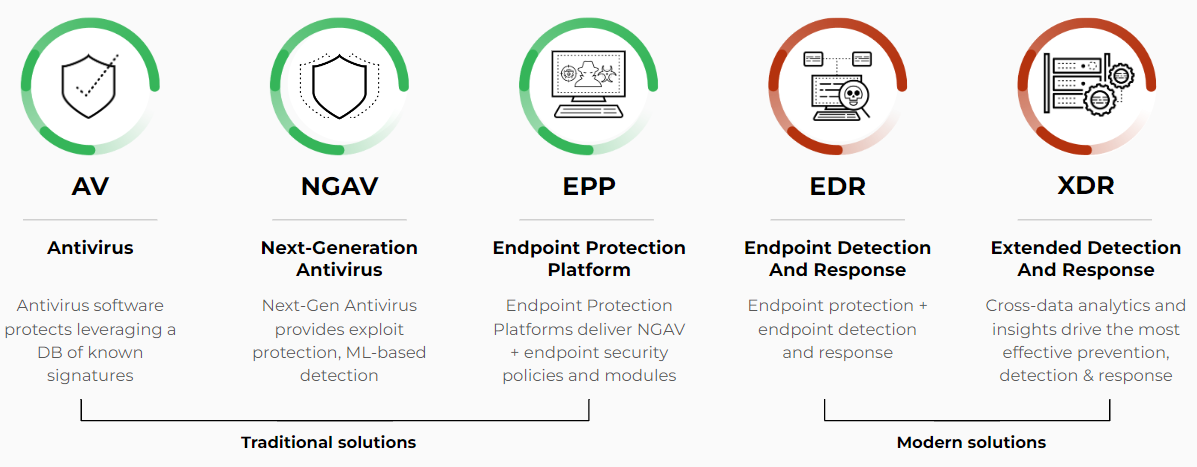
Traditional vs. Cloud Native EPPs
Traditional and cloud-native Endpoint Protection Platforms (EPPs) differ primarily in their architecture, deployment, and management models. Here are the key distinctions between the two:
Traditional EPPs
On-Premises: Traditional EPPs are typically installed on local servers within an organization's data center. These EPPs often rely heavily on client-side agents installed directly on endpoint devices.
Deployment can be more complex and time-consuming, requiring significant IT resources for installation, configuration, and ongoing maintenance. Updates to the software and threat definitions are often manually managed or require periodic downloads and installations.
Management is usually done through a local console or server-based management interface. Scaling up can be challenging and may require additional hardware investments.
Traditional EPPs can also be resource-intensive, potentially affecting the performance of endpoint devices. Due to their reliance on local resources, there are potential latency issues in threat detection and response.
Traditional EPPs:
- On-premises deployment requiring local infrastructure
- Complex installation and maintenance processes
- Manual updates and threat definition management
- Resource-intensive on endpoint devices
- Limited scalability requiring hardware investments
Cloud Native EPPs
Cloud-native Endpoint Protection Platforms (EPPs) use cloud technology to offer scalable and flexible device security. These platforms rely on lightweight software agents installed on endpoint devices that connect to cloud services.
Deployment is fast and easy, and little to no on-site hardware is needed. The cloud automatically manages software and threat updates, protecting devices with the latest security features. Users manage everything through a centralized cloud console accessible from anywhere, simplifying administrative tasks.
Cloud-native EPPs are highly scalable. Organizations can quickly add or remove devices without needing extra hardware. They are also efficient, having a more minor impact on device performance. Thanks to continuous cloud connectivity and advanced analysis, they provide better real-time threat detection and response.
Key Differences
- Deployment Model: Traditional EPPs require on-premises infrastructure, while cloud-native EPPs leverage cloud services.
- Management: Traditional EPPs use local management consoles, whereas cloud-native EPPs offer centralized cloud-based management.
- Scalability: Cloud-native EPPs provide greater scalability and flexibility.
- Performance Impact: Cloud-native EPPs have a lower impact on endpoint performance and offer real-time updates and threat detection.
EPP vs EDR: A Comparative Analysis
EPP and Endpoint Detection and Response (EDR) are integral components of modern cybersecurity strategies that provide comprehensive endpoint security, which is crucial for defending against sophisticated cyber threats that continue to evolve.
EPP prevents security threats as a proactive barrier that stops malware and unauthorized access at the endpoint level. EPP is designed to prevent threats from ever touching the network using techniques like antivirus scanning, firewalls, and behavior monitoring.
EDR specializes in identifying and reacting to threats by providing detailed forensics and analysis to address breaches quickly. It focuses on detecting and responding to threats that have already breached the defenses. It offers deep visibility and digital forensics capabilities, allowing organizations to understand and mitigate attacks in real time.
The two systems complement each other: EPP’s preventive measures help reduce threat exposure, while EDR's advanced monitoring and response capabilities ensure rapid threat mitigation and recovery. Integrating EPP with EDR enables seamless coordination, facilitating swift incident remediations and minimizing damage, ultimately strengthening an organization's cybersecurity framework.
Case Studies: Real-World Applications
A global financial institution deployed an advanced EPP and successfully thwarted a sophisticated phishing attack that aimed to compromise sensitive customer data. The EPP's robust threat detection capabilities and real-time monitoring features enabled the IT team to identify and neutralize the threat swiftly.
In another scenario, a large healthcare provider implemented EPP solutions to ensure compliance with stringent data protection regulations while mitigating ransomware attack risks. The platform's ability to provide comprehensive endpoint visibility and automated response actions was crucial in maintaining the integrity and security of patient information.
These examples demonstrate how EPPs enhance an organization's cybersecurity posture and bolster its operational resilience in the face of digital adversities.
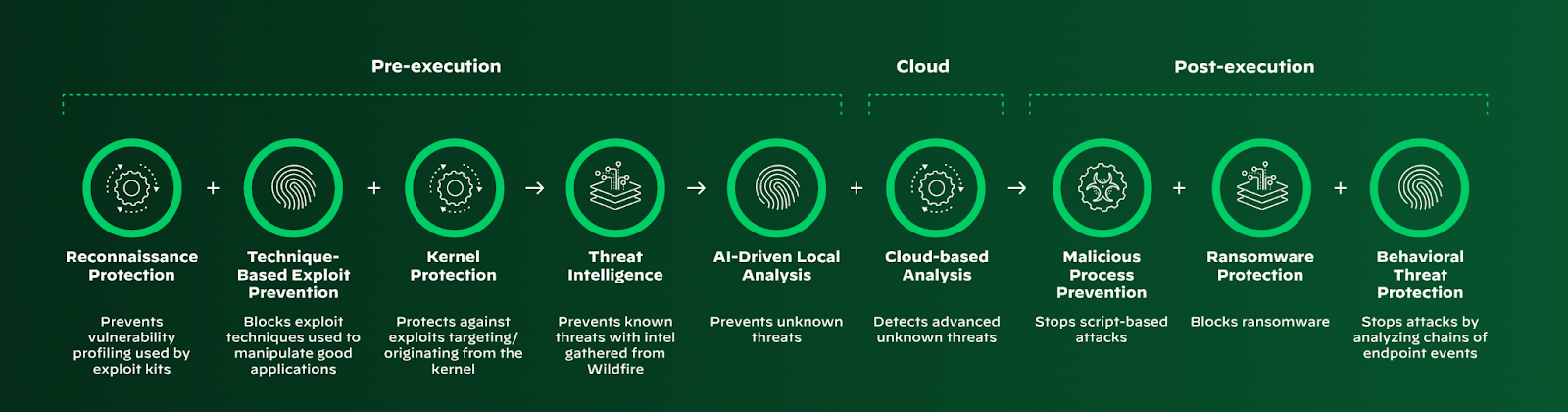
AI-powered cybersecurity pipeline that detects and responds to threats across the complete attack lifecycle, from initial reconnaissance through post-execution behavioral analysis and remediation.
How to Choose the Best EPP
Choosing the right EPP is essential for enhancing organizational cybersecurity. Key features should be evaluated based on the number of endpoints, and the provider's support is critical.
Testing the platform in real-world scenarios can reveal user-friendliness and management interface effectiveness. Additionally, seeking feedback from IT teams and reviewing third-party evaluations can provide valuable insights into the platform's strengths and weaknesses.
Evaluating Key Features
When evaluating an EPP's key features, several core components that ensure comprehensive security must be considered:
- Look for comprehensive threat detection and prevention capabilities, including real-time monitoring and identifying known and unknown threats through advanced threat intelligence.
- Ease of deployment across a diverse range of devices and operating systems is essential, as it ensures seamless integration with existing IT infrastructure without causing disruptions.
- Consider the platform's ability to provide a centralized management console, which would simplify oversight and allow for efficient policy enforcement and updates across all endpoints.
- Interoperability with other security solutions is also essential, as it enhances the overall security posture by enabling coordinated responses to potential incidents.
- User-friendly reporting and analytics tools can provide valuable insights into the security environment, helping to fine-tune protection strategies and anticipate future challenges in maintaining endpoint security.
Testing and Evaluation Tips
When testing and evaluating EPPs, it is best to adopt a structured approach that aligns with your organization's security needs and IT environment.
- Begin by clearly defining your objectives and the specific security challenges you need the EPP to address. This focus will help narrow down the list of potential solutions.
- Engage in a comprehensive testing phase, including real-world scenario simulations, ensuring the platform performs effectively against known threats and zero-day vulnerabilities. During this process, pay special attention to the platform's ease of deployment and integration capabilities.
- Ease of use is just as important as the technology itself, as a user-friendly interface can significantly reduce the learning curve for administrative staff.
- Consider the vendor's customer support and response times, as ongoing support is vital for maintaining resilient security defenses.
- Gather end-user feedback for insights on usability and performance to make a well-informed decision.