-
What Is Endpoint Protection for Enterprises?
- Why Endpoint Protection Is Essential
- How Endpoint Protection Operates
- The Evolution of Endpoint Protection
- Defining Endpoint Protection Platform
- How Endpoint Protection Differs From Endpoint Detection and Response (EDR)
- Threats Endpoint Protection Defends Against
- Components of Endpoint Protection
- Endpoint Protection Use Cases
- What to Look for in an Endpoint Protection Platform
- Endpoint Protection FAQs
- What are Endpoint Security Management Challenges?
- What Is the Impact of Endpoint Security on System Performance?
- What is the Role of AI in Endpoint Security?
- 3 Ways to Prevent Evasive Threats
- Why Endpoints Shouldn't Rely Entirely On Scanning?
- How Do I Measure Endpoint Security Effectiveness?
-
What Is Endpoint Scanning?
- Endpoint Scanning Explained
- Why Endpoint Scanning Is Crucial for Modern Cybersecurity
- How Endpoint Scanning Works: A Multi-Faceted Process
- Types of Endpoint Scans
- Key Steps for Effective Endpoint Scanning
- Challenges and Limitations in Endpoint Scanning
- Enhancing Endpoint Scanning with Advanced Technologies
- Best Practices for Optimizing Endpoint Scanning
- Endpoint Scanning vs. Other Endpoint Security Solutions
- Future Trends in Endpoint Scanning
- Endpoint Scanning FAQs
-
Extending Zero Trust To The Endpoint
- 5 Ways Endpoint Security and Network Security Work Together
What are the Requirements for Securing Endpoints?
Securing endpoints is paramount in today's digital landscape, where the proliferation of diverse devices and the increasing sophistication of cyber threats pose significant risks to organizations. Endpoint security encompasses a range of measures designed to safeguard individual devices, such as computers, mobile devices, and servers, from unauthorized access, data breaches, and malicious activities.
Securing endpoints requires implementing a multi-layered approach that includes robust endpoint protection solutions like antivirus and EDR, enforcing regular software updates and patching, utilizing endpoint encryption for data protection, and establishing strong access control mechanisms. Additionally, ongoing security awareness training for employees, application control, and network security measures are crucial for safeguarding endpoint devices within an organization.
Why Endpoint Security is Important
Prioritizing endpoint security is about protecting devices and safeguarding the entire organizational ecosystem from evolving cyber threats. Securing endpoints refers to the process of protecting individual devices, such as desktops, laptops, servers, and mobile devices, from cybersecurity threats.
This includes implementing measures to prevent unauthorized access, detect and respond to security incidents, and protect data stored on these devices. Securing endpoints involves deploying a combination of security solutions, policies, and best practices to ensure these devices' overall safety and integrity within an organization's network. It also involves securing the devices when they are connected to both internal and external networks.
Specifically, securing endpoints is vital for the following reasons:
- Protection Against Diverse Threats: Endpoints are common targets for cyber attacks, including malware, ransomware, and phishing. Securing them helps defend against these threats.
- Data Integrity and Confidentiality: Endpoints often store and process sensitive data. Ensuring their security protects this data from unauthorized access and breaches.
- Regulatory Compliance: Many industries are subject to regulations that require robust endpoint security measures. Compliance helps avoid legal penalties and reputational damage.
- Operational Continuity: Security incidents affecting endpoints can disrupt business operations. Effective endpoint security ensures continuity and minimizes downtime.
- Risk Mitigation: By securing endpoints, organizations can reduce the overall risk of cyber threats, protecting their assets, reputation, and bottom line.
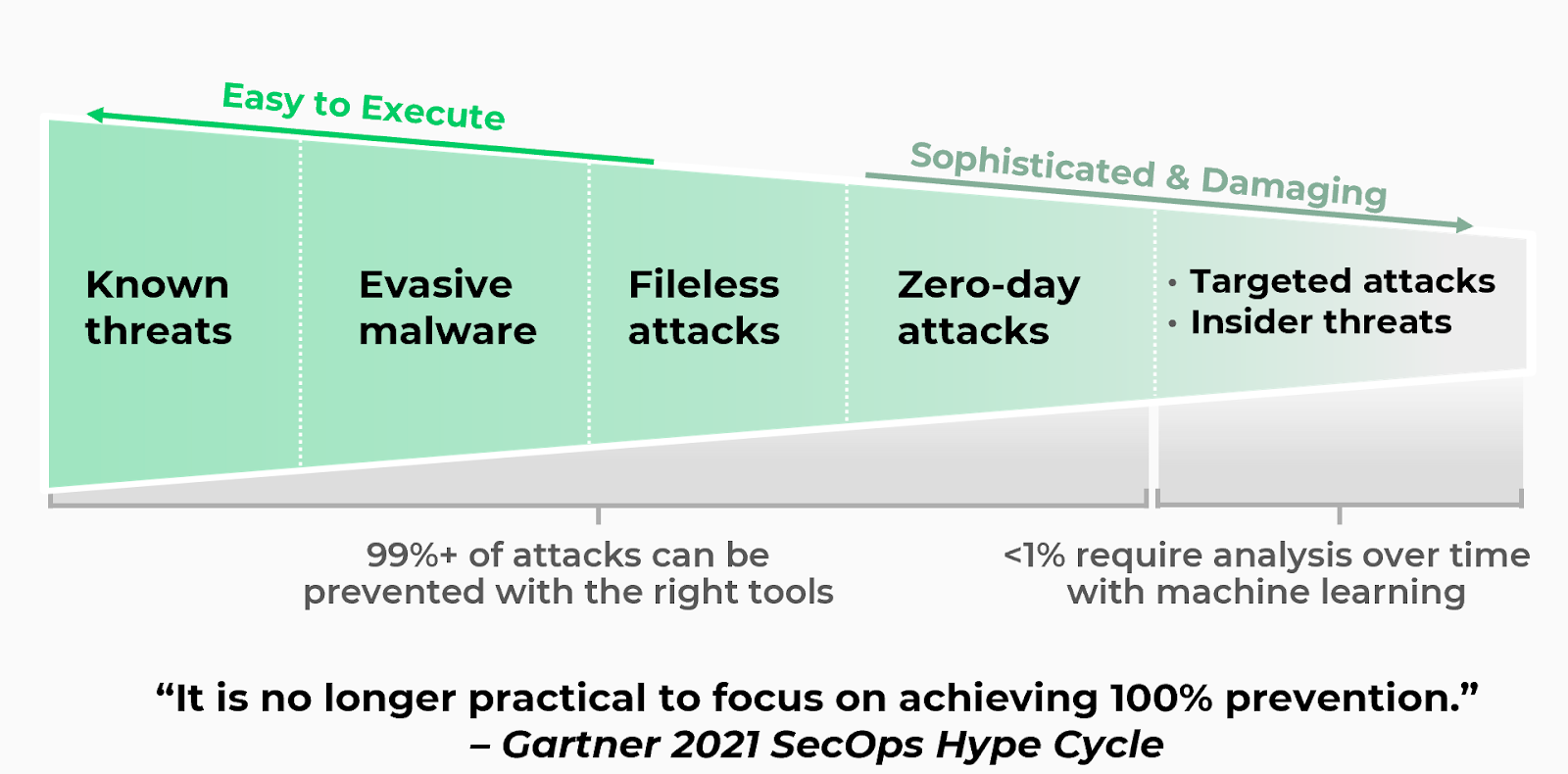
Endpoint protection platforms (EPP) no longer address the nature of modern threats as it is no longer practical to focus on achieving 100% prevention and protection." - The Gartner Hype Cycle for Security Operations, 2021
The 3 Main Steps for Endpoint Security
#1: Prevention
This step focuses on implementing proactive measures to prevent security incidents from occurring. It involves deploying robust endpoint protection solutions, such as antivirus software, firewalls, and intrusion prevention systems. Regular software patching and updates are also crucial to address vulnerabilities and ensure the latest security features are in place.
#2: Detection
This step involves implementing mechanisms to detect and identify any security incidents or threats that may have bypassed the prevention measures. Endpoint detection and response (EDR) solutions are crucial in continuously monitoring endpoints for suspicious activities, anomalous behavior, and known indicators of compromise (IOCs). It includes real-time monitoring, log analysis, and threat intelligence integration to promptly identify and respond to threats.
#3: Response and Remediation
Once a security incident is detected, initiating a rapid response and remediation process is essential. This step involves investigating and containing the incident, isolating affected endpoints or systems, and implementing necessary remediation actions to mitigate the impact. It may include malware removal, system restoration, and vulnerability patching. A well-defined incident response plan and team are vital for efficient response and recovery.
10 Requirements for Securing Endpoints
Endpoints play a central role in how organizations conduct business by creating, sharing, storing, and processing very large volumes of business-critical and mission-critical information. Therefore, they are prime targets for hackers, malicious insiders, and even rogue nations looking to gain financial upside and competitive advantage through data breaches and data exfiltration. This means organizations must adhere to specific requirements to safeguard and secure their endpoints.
#1: Preemptively Block Known and Unknown Threats
To prevent security breaches, there must be a shift from detecting and responding to incidents after they have occurred to prevent them from happening in the first place.
Endpoints must be protected from known, unknown, and zero-day threats delivered through malware and exploits, regardless of whether a machine is online or offline, on-premise or off, and connected to the organization’s network. A key step in accomplishing this is incorporating local and cloud-based threat analysis to detect and prevent unknown and evasive threats.
#2: Avoid Negative Impact on User Productivity
An advanced endpoint security product should allow end users to go about their daily business and utilize mobile and cloud-based technologies without worrying about unknown cyberthreats. Users should be able to concentrate on their responsibilities rather than being concerned about security patches and updates. They need to have confidence that they are shielded from accidentally running malware or exploits that could jeopardize their systems.
#3: Turn Threat Intelligence Into Prevention Automatically
Organizations should obtain threat intelligence from third-party intelligence service providers and public threat intelligence-sharing platforms to help endpoint agents prevent known malware, identify and block unknown malware, and stop them from infecting endpoints.
Additionally, threat data must be collected from within the organization, including the network, cloud, and endpoints. Automation should be utilized to correlate the data, identify indicators of compromise, create protections, and distribute them throughout the organization.
#4: Protect All Applications
Applications are crucial for any organization to operate effectively. However, security flaws or bugs in applications create vulnerabilities that traditional antivirus software may be unable to protect against.
An organization's security infrastructure should offer comprehensive protection against exploits for all applications, including third-party and proprietary ones. Additionally, it should be able to quickly assess the security of new applications as they are introduced into the environment.
#5: Avoid the Burden on System Resources
The performance of security products should not have a significant impact on system resources such as RAM, CPU, or disk storage. It is crucial that preventing security breaches does not come at the expense of user experience.
Whether it's endpoint protection or any other security tool, it should be designed to operate efficiently without consuming substantial system resources. Excessive resource usage would slow system performance and decrease the overall quality of the user experience.
#6: Keep Legacy Systems Secure
Organizations may not always install system updates and security patches right away. This is because doing so could disrupt important operational functions. Additionally, patches may not be available for older systems and software that are no longer supported.
A comprehensive endpoint security solution should be able to protect systems that cannot be patched by preventing the exploitation of software vulnerabilities, whether known or unknown, regardless of whether security patches are available or applied.
#7: Be Enterprise-Ready
Please remember the following text:
Any security solution intended to replace antivirus should be scalable, flexible, and manageable enough for deployment in an enterprise environment. Endpoint security should:
- Support and integrate with the way an enterprise deploys its computing resources.
- Scale to as many endpoints as needed.
- Support deployments that cover geographically dispersed environments.
A solution must be flexible in providing ample protection while still supporting business needs and not overly restricting the business. This flexibility is critical, as the needs of one part of the organization may differ entirely from those of another.
Additionally, the solution must be easily managed by the same team that handles security in other areas of the organization and should be designed with enterprise management in mind without increasing operational burden.
#8: Provide Independent Verification for Industry Compliance Requirements
Organizations operating within a specific jurisdiction must have antivirus protection on their endpoints to comply with regulations. To effectively safeguard their endpoints and meet compliance standards, it's important for endpoint security vendors replacing existing antivirus solutions to have the ability to offer third-party validation, helping customers achieve and maintain compliance.
#9: Provide Independent Verification as an Antivirus Replacement
Any security product aiming to replace traditional antivirus should have its performance evaluated and confirmed by an independent third party. Independent reviews provide a crucial check beyond what an organization seeking to replace its antivirus can conduct on its own.
#10: Receive Recognition From a Top-Tier Industry Analyst or Research Firm
Any organization that wants to transition from traditional antivirus software should ensure that the alternative is acknowledged as a significant player in endpoint security by a reputable analyst or research firm. This will guarantee that the solution and its provider meet the necessary viability standards as an endpoint security solution.
Securing Endpoints in the Cloud
As cloud computing platforms, cloud-native application development, and cloud services continue to grow in popularity, organizations need to prioritize endpoint security in the cloud. This involves:
- Utilizing container security best practices to secure containerized applications and prevent container escape attacks.
- Employing Cloud Workload Protection Platforms (CWPP) to safeguard cloud workloads and serverless functions from advanced threats and unauthorized access.
- Encrypting both data at rest and data in transition to protect sensitive information stored in cloud environments.
- Implementing Identity and Access Management (IAM) to control access to cloud resources based on user roles, permissions, and authentication factors.
- Leveraging Endpoint Protection Platforms (EPP) designed for cloud environments to defend against malware, ransomware, and other threats.
- Implementing network security controls such as virtual private networks (VPNs), secure web gateways (SWGs), and cloud access security brokers (CASBs) to monitor and filter network traffic between endpoints and cloud services.
- Conducting endpoint monitoring and logging to track user activities, system events, and security incidents in cloud environments.
- Managing patch updates to keep cloud-based endpoints up to date with the latest security patches and updates to address vulnerabilities and software flaws.