-
What Is Endpoint Detection and Response (EDR)?
- Understanding EDR
- Key Benefits of EDR Solutions
- How EDR Works: A Detailed Breakdown
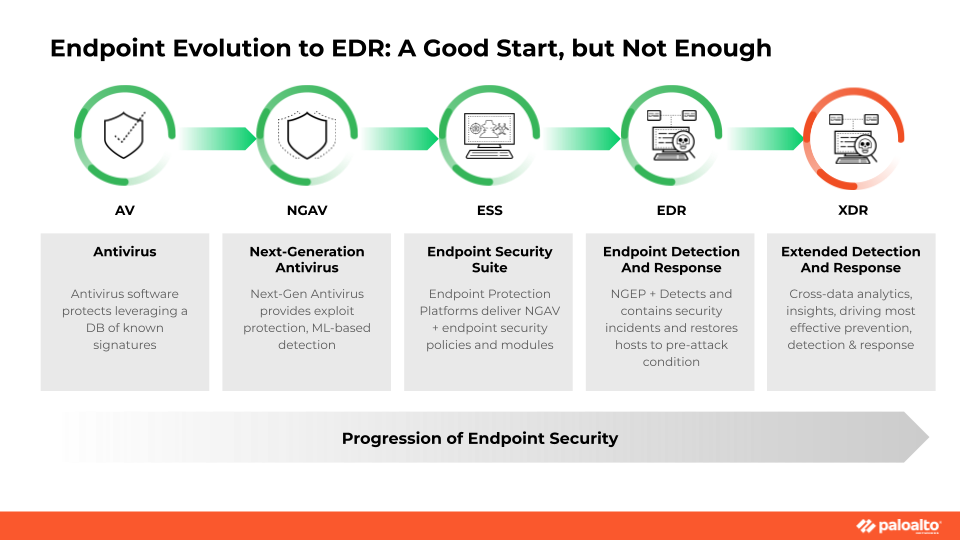
- Evolution of EDR
- EDR Implementation Process
- Common Challenges and Solutions in EDR Adoption
- Advanced EDR Strategies and Optimization Techniques
- EDR and the Evolving Threat Landscape
- How to Evaluate an EDR Solution
- EDR FAQs
-
What Is Endpoint Detection and Response (EDR) Management?
- EDR Management Explained
- Key Capabilities of EDR Management
- The Crucial Role of EDR Management in Modern Cybersecurity
- EDR Management Challenges and Solutions
- Best Practices for Effective EDR Management
- EDR vs. EPP: A Complementary Relationship
- Integrating EDR Management with a Broader Security Ecosystem
- Case Study of a Successful EDR Implementation
- EDR Management FAQs
- What Is Endpoint Detection and Response (EDR) Deployment?
- What is EDR-as-a-Service Managed Security?
- What Are Endpoint Detection and Response Tools?
- How Does EDR Enhance Small Business Cybersecurity?
- How Does EDR Leverage Machine Learning?
- What Is Endpoint Detection and Response (EDR) Compliance?
- What is the Difference Between EDR vs. SIEM?
- What is EDR vs. XDR?
What is EDR vs. Antivirus?
EDR (Endpoint Detection and Response) and traditional Antivirus software protect computers and networks from malware and other threats, but they provide different levels of defense.
Here are the main differences between EDR (Endpoint Detection and Response) and antivirus software:
Purpose:
- Antivirus: Targets known malware using signature-based detection.
- EDR: Monitors, detects, and responds to a broader range of threats, including sophisticated attacks.
Detection Methods:
- Antivirus: Relies on signatures to identify threats.
- EDR: Uses behavioral patterns and anomaly detection for identifying advanced threats.
Response Capabilities:
- Antivirus: Focuses on removing malware.
- EDR: Includes real-time containment and detailed investigation tools.
Scope of Protection:
- Antivirus: Limited to file and program integrity.
- EDR: Offers broader protection with forensic tools and network-wide analysis.
User Interaction:
- Antivirus: Minimal; operates automatically.
- EDR: Requires skilled personnel for effective management and response.
These distinctions highlight EDR’s role in providing a deeper and more dynamic approach to cybersecurity than traditional antivirus solutions, which focus more on static, signature-based malware detection.
What is Antivirus?
While EDR offers real-time, around-the-clock monitoring and responds to known and emerging threats, traditional antivirus primarily focuses on known threats, preventing, detecting, and removing malicious software like viruses, worms, and trojans. Using various methods, they identify malicious software or code that has infected a computer.
Detection Methods
Antivirus software uses three methods to detect malware: signature-based, heuristic-based, and behavioral-based detection. Signature-based detection is the more traditional method, using a database of known malware signatures.
Signature-Based Detection
These signatures are unique data strings or code sequences characteristic of specific malware. When a file matches a signature in the database, it is flagged as malicious. However, this method requires regular database updates to remain effective against new threats.
Heuristic-Based Detection
This method is used to catch malware that has not yet been formally identified and added to the signature database. It involves looking for patterns or behaviors typical of malicious software. For example, a program trying to modify system files or hide its presence might be flagged.
Behavioral-Based Detection
This approach monitors the behavior of programs and files in real-time. Suppose a program starts acting suspiciously, such as trying to access sensitive data or modify system settings without permission. In that case, the antivirus can detect this as potential malware, even if the program isn’t in its signature database.
Prevention and Blocking
Antivirus programs provide real-time scanning by running in the background and scanning files as they are opened, created, or downloaded. This helps prevent malware from executing and causing damage. Additionally, many antivirus solutions come with web shields that scan and block malicious websites or downloads before they can cause harm.
Removal and Quarantine
Antivirus software can detect potentially harmful software and move it to a quarantine area, which isolates the file from the rest of the system. This prevents the software from causing further damage while allowing the user to review and delete it if necessary. Additionally, antivirus software can often automatically clean infected files, removing malicious content while preserving the original data.
System Scans and Updates
Antivirus software can be configured to perform complete system scans at regular intervals, which can be scheduled according to the user's needs. Additionally, users can manually initiate scans when necessary. Since new malware is constantly being developed, antivirus software must regularly update its database of malware signatures and algorithms to detect newer threats. These updates are typically downloaded automatically from the vendor's servers.
Antivirus software plays a crucial role in cybersecurity defense strategies, especially for blocking known threats and providing a first line of defense against potential infections. However, given the ever-evolving nature of cyber threats, antivirus is most effective with other security measures, such as firewalls, anti-spyware programs, and comprehensive security practices.
What is EDR?
EDR provides a more comprehensive and dynamic approach to protecting endpoints from various cyber threats, including sophisticated malware, ransomware, and targeted attacks.
Operational Aspects of EDR
EDR systems operate through a combination of technology and strategies to provide real-time monitoring and response capabilities. Here’s a detailed look at the operational aspects of EDR:
Data Collection
EDR tools continuously collect and record data from endpoints in real-time. This data includes process executions, network connections, registry changes, file modifications, and other relevant system activities. The depth of data collected is much greater than traditional antivirus software.
Threat Detection
- Behavioral Analysis: EDR systems analyze the behavior of processes and communications on endpoints to identify anomalies that could indicate a threat. This includes looking for unusual patterns such as sudden increases in data transmission, unexpected processes launching at startup, or unauthorized attempts to access sensitive data.
- Anomaly Detection: Using machine learning and statistical modeling, EDR solutions can detect deviations from normal operations, identifying potentially malicious activities that don't match known malware signatures.
- Threat Intelligence Integration: EDR platforms often integrate with external threat intelligence feeds to enhance detection capabilities. This helps identify known malicious entities (like IP addresses or domains) and correlate observed behaviors with known threat patterns.
Alerts and Notifications
When suspicious activity is detected, EDR systems generate alerts and provide detailed context about the incident. This can include information about the affected endpoint, the nature of the suspicious activity, and potential impact. These alerts enable security analysts to understand and prioritize threats quickly.
Response and Mitigation
- Automated Responses: EDR tools can execute predefined response actions automatically when a threat is detected. These actions might include killing malicious processes, quarantining infected files, isolating compromised endpoints from the network, or reversing unauthorized changes.
- Manual Intervention: EDR provides tools for security analysts to remotely access affected endpoints, conduct detailed investigations, and manually remediate issues. Analysts can execute commands, gather additional forensic data, and apply patches or updates.
Forensics and Investigation
- Timeline Analysis: EDR systems provide a detailed timeline of events leading up to and following a security incident. This allows security teams to trace the root cause of an attack and understand the scope of a breach.
- Search Capabilities: Analysts can search across collected data using various criteria to identify related events or patterns across the network.
Continuous Improvement
Insights gained from investigations and daily operations are used to refine detection algorithms, improve response strategies, and update security policies.
EDR solutions are particularly effective when organizations face sophisticated and evolving threats. They are designed to detect and react to threats and provide the tools necessary for deep forensic analysis and ongoing improvement of security postures.
Use Cases for Antivirus
Despite its limitations compared to EDR solutions, antivirus software offers an excellent defense mechanism for several essential use cases.
Organizations face two significant challenges at the endpoint - malware protection and email security. Antivirus software effectively detects and removes various known malware types, including ransomware, adware, viruses, and more. Additionally, antivirus software continuously scans emails for potential threats, making inspecting email attachments and links for potential problems more manageable.
Other important use cases for antivirus include:
- Safe web browsing
- Scheduled scanning
- Automatic endpoint security updates
- Scanning of external storage devices such as USB drives
- Real-time scanning
- Firewall integration
- Parental controls
- Multi-platform protection
Use Cases for EDR
EDR's versatility makes it suitable for a large number of use cases. One such use case is cloud endpoint security, as more organizations now have endpoints in the cloud and need a cloud-friendly platform for detection and response.
This extension of an organization's infrastructure to the cloud makes other use cases a good match for EDR. These include threat hunting, ransomware protection, phishing/credentials theft, and multi-platform protection.
Another excellent use case for EDR is insider threat detection, as malicious insiders can use their endpoint privileges to move laterally throughout an organization's network, applications, and web services.
EDR also effectively detects Zero Day threats, using sophisticated techniques such as machine learning algorithms and heuristic analysis to spot and track threats that lack known signatures.
Additional use cases where EDR makes sense include:
- Incident response automation
- Forensic analysis
- Real-time threat detection
- Incident investigation
- Security posture assessment
- Compliance and reporting
- Automated patch management
How EDR Differs From MDR and XDR
The subsequent logical extensions of traditional EDR are Managed Detection and Response (MDR) and Extended Detection and Response (XDR). All three are essential elements to an organization's enterprise-wide cybersecurity framework, and many organizations use all three solutions together for a multilayered defense.
MDR is a managed service provided by third-party organizations and often operated in tight collaboration with in-house cybersecurity teams. It detects and responds to cybersecurity threats across the organization's digital infrastructure—endpoints, networks, cloud gateways, and more. EDR solutions are often a key part of this managed service.
XDR is an even more comprehensive approach to cybersecurity because it addresses threats across an organization's entire IT landscape and includes data from multiple security tools throughout the enterprise.
Their main differences are:
- EDR is endpoint-focused, XDR addresses threats on all parts of the organization's technology platforms, and MDR is a third-party-managed service for monitoring and incident response, often including EDR tools.
- EDR is often deployed on in-house infrastructure using internal security team members; MDR is an outsourced service, and XDR can be deployed and managed internally or through a third party.
Many organizations employ an EDR solution with MDR and XDR for a more holistic, end-to-end cybersecurity strategy.