-
- Vulnerability Management Explained
- Why Cloud Vulnerability Management Is Challenging
- How Vulnerability Management Has Evolved
- Vulnerability Management Vs. Patch Management
- Overview of Common Vulnerabilities and Exposures (CVEs)
- Vulnerability Management Vs. Vulnerability Assessment
- The Vulnerability Management Lifecycle
- Best Practices for Managing Cloud Workload Vulnerabilities
- Setting Up a Vulnerability Management Framework
- Building a High-Performance Program
- Technology Stack and Integration Requirements
- Vulnerability Management FAQs
Table of content
-
What Is Patch Management? Process, Policy, and Benefits
- Understanding Patch Management
- Why Patch Management Is Important
- The Patch Management Process
- Patch Management in Cloud and Hybrid Environments
- Key Patch Management Challenges and How to Solve Them
- How to Create an Effective Patch Management Policy
- Leveraging Tools and Technologies for Patch Management
- CWPPs and Patch Management
- Patch Management FAQs
-
What Is Risk-Based Vulnerability Management?
- Risk-Based Vulnerability Management Definition
- Why Organizations Need a Risk-Based Approach?
- Key Components of a Risk-Based Vulnerability Management Framework
- From Discovery to Remediation — RBVM in Practice
- Benefits of Adopting a Risk-Based Vulnerability Management Strategy
- Risk-Based Vulnerability Management FAQs
- Vulnerability Management Program: Building a Risk-Based Framework
- What Is Vulnerability Scanning?
-
Patch Management Vs. Vulnerability Management
- Patch Management and Vulnerability Management Definition
- Key Differences Between Patch and Vulnerability Management
- Where They Overlap — Coordination Is Key
- How to Build an Integrated Patch and Vulnerability Management Strategy
- Tools That Bridge Vulnerability and Patch Management
- Patch Management vs. Vulnerability Management FAQs
-
What Is Threat and Vulnerability Management?
- Threat and Vulnerability Management
- Key Components of a Threat and Vulnerability Management Program
- Comparing Threat and Vulnerability Management by Risk Elimination
- The Value of Integrated Threat and Vulnerability Management
- Building a Threat and Vulnerability Management Strategy
- Threat and Vulnerability Management FAQs
- Vulnerability Management Lifecycle: Key Phases and Execution
-
How to Automate Vulnerability Management Steps, Tools, and Benefits
- Understanding Vulnerability Management Automation
- The Four Pillars of Automated Vulnerability Management Workflow
- Tools and Technologies for Vulnerability Remediation Automation
- Benefits of Vulnerability Management Automation
- Challenges and Best Practices for Implementation
- How to Automate Vulnerability Management FAQs
-
What Is Continuous Vulnerability Management (CVM)?
- Understand Continuous Vulnerability Management
- CVM Vs. Traditional Vulnerability Management
- When to Consider Continuous Vulnerability Management
- How CVM Works in Enterprise Environments
- Key Benefits of CVM
- Challenges of CVM Adoption
- Best Practices for CVM Adoption
- Continuous Vulnerability Management (CVM) FAQs
What Is Vulnerability Management?
5 min. read
Table of content
Vulnerability management governs how organizations identify, evaluate, prioritize, and reduce weaknesses across their digital estate, including code, cloud services, on-premises systems, identities, and third-party integrations. Functioning as a continuous risk discipline that aligns discovery and remediation to real attack paths, vulnerability management prevents system intrusions and data breaches, in addition to other adverse incidents, ultimately elevating security teams from a reactive, day-late posture to an effective and formidable security offense.
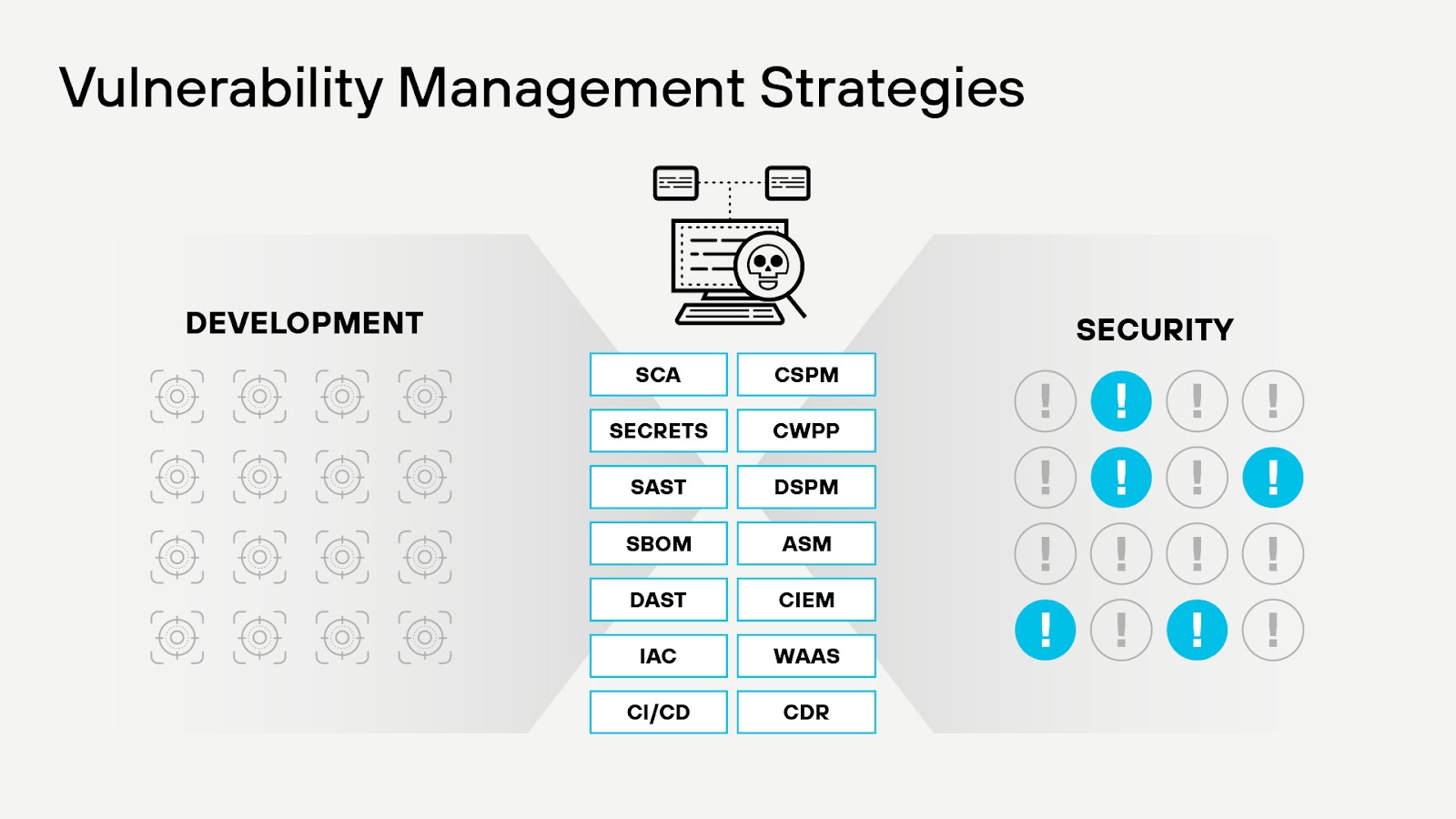
Figure 1: Vulnerability management comprises diverse technologies and security measures across the application lifecycle.
Vulnerability Management Explained
Vulnerability management operates as a continuous discipline that identifies, analyzes, and reduces weaknesses across every layer of an organization’s digital environment. It covers network devices, servers, storage systems, workstations, legacy applications, virtual machines, containers, cloud applications, microservices, databases, APIs, identity systems, third-party components, cloud infrastructure and cloud platform services, security configurations, and more.
The process begins with maintaining an up-to-date asset inventory and employing vulnerability scanning to discover potential threats in cloud resources. Vulnerabilities are then assessed based on their severity and impact, allowing for prioritization of remediation efforts. Patch and configuration management address software vulnerabilities and misconfigurations, while continuous monitoring and incident response ensure the rapid detection and containment of emerging threats. Lastly, reporting and auditing activities provide visibility and accountability, ensuring the effectiveness and compliance of the vulnerability management program.
Note: The vulnerability management program thrives only when it produces accurate visibility, ranks issues by real-world exploitability, and drives timely remediation that aligns with how systems evolve.
Security teams rely on discovery pipelines that monitor configuration states, software inventories, dependency graphs, entitlements, and runtime behavior. Each source feeds a unified risk model that highlights where attackers can gain a foothold. Accuracy depends on correlating signals rather than treating each technology stack in isolation.
Exposure Lifecycle
Effective programs track a vulnerability from introduction to remediation. Analysts need context on where the flaw originated, how it propagates across workloads, and which controls can contain it before a fix lands. A rapid cycle shortens the period in which adversaries can act.
Operational Coordination
Sustained performance requires coordination among security engineers, platform teams, and developers. Remediation plans must reflect operational constraints, deployment schedules, and service dependencies. Programs that integrate with CI systems, infrastructure orchestration, and asset governance platforms keep risk reduction aligned with delivery velocity.
Why Cloud Vulnerability Management Is Challenging
Vulnerability management isn’t simple, regardless of workload type. But, when you’re dealing with cloud workloads, detecting and mitigating vulnerabilities is especially challenging.
Cloud Services Are Complex and Varied
Cloud workloads may include VMs, containers, serverless functions, orchestration services, or all of the above. Each type of cloud workload could be subject to different types of vulnerabilities, so you need a vulnerability management strategy that can recognize different threats based on workload context.
Effective vulnerability management demands scanning across infrastructure, platform, and application layers simultaneously. A containerized application running on Kubernetes in AWS presents vulnerabilities at the container image level, the Kubernetes configuration level, the EC2 instance level, the VPC network level, and the IAM policy level. Each layer requires different assessment techniques and remediation workflows.
Infrastructure-as-code repositories contain vulnerabilities before deployment occurs. Terraform modules with overly permissive security group rules or CloudFormation templates missing encryption configurations inject vulnerabilities directly into production. Vulnerability management tools must integrate with version control systems to detect misconfigurations before infrastructure provisioning.
Cloud Environments Are Dynamic
Containers and serverless functions exist for minutes or hours before termination, creating temporal blind spots in periodic vulnerability scanning. A container spawned at 2:00 PM and terminated at 2:45 PM evades a vulnerability scanner running at 3:00 PM. Vulnerability management platforms designed for cloud environments must scan workloads during their brief lifespans or shift assessment upstream into container registries and CI/CD pipelines.
Autoscaling compounds the problem. Kubernetes clusters expand from 10 pods to 500 pods during traffic spikes, then contract within minutes. Each ephemeral instance carries its own vulnerability profile. Agentless technologies that read runtime block storage provide discovery without requiring software installation on short-lived compute resources.
Shared Responsibility and Visibility Gaps
The shared responsibility model in cloud environments creates ambiguity about which vulnerabilities organizations own. Cloud providers patch hypervisor vulnerabilities and managed service infrastructure, but customers own guest OS patching, application security, and configuration management. Managed database services obscure the underlying infrastructure, limiting vulnerability visibility while still requiring proper access controls and encryption.
Third-party SaaS applications integrated via APIs introduce vulnerabilities outside organizational control. When SaaS vendors patch slowly or fail to disclose vulnerabilities, customers inherit risk without remediation authority. Vulnerability management in cyber security must account for these external dependencies through vendor risk assessment and continuous SaaS security monitoring.
API and Serverless Function Vulnerabilities
APIs serve as the connective tissue in cloud architectures, and vulnerabilities in authentication, authorization, and rate limiting create exploitable attack surfaces. Broken object-level authorization allows attackers to access resources belonging to other users. Missing function-level access controls enable privilege escalation. API-specific vulnerability scanning requires understanding business logic and data flow rather than just scanning for known Common Vulnerabilities and Exposures (CVEs).
Serverless functions execute code without persistent infrastructure, complicating vulnerability management processes. Functions pull dependencies from external repositories at runtime. A compromised npm package or Python library injects vulnerabilities into every function invocation. Security vulnerability management for serverless demands dependency scanning, secrets management, and runtime protection simultaneously.
Cloud environments amplify lateral movement risk when vulnerabilities exist across multiple layers. An exposed API endpoint combined with excessive IAM permissions creates an attack path to sensitive data stores. Effective vulnerability management in the cloud requires attack path analysis that maps how isolated vulnerabilities connect into exploitable chains.
How Vulnerability Management Has Evolved
Scale broke traditional programs. Consider that vulnerability disclosures amounted to 70,000 new CVEs in 2025, averaging 130 daily flaws and reaching record highs. The volume reflects an exploding attack surface where the time-to-exploit has collapsed. High-profile bugs now see weaponization within 24 hours. While legacy issues like XSS persist, the emergence of rapid-fire exploits like React2Shell highlights a shift toward immediate, automated exploitation of newly discovered vulnerabilities. Under this volume, traditional vulnerability management built around monthly patch cycles and CVSS severity scores have reached their breaking point.
Cloud architectures magnify risk because individual weaknesses rarely exist in isolation. A misconfigured S3 bucket exposes sensitive data directly to the internet. A container running with excessive privileges opens lateral movement paths to production databases. An API endpoint with broken authentication or missing rate limiting allows credential stuffing attacks. Each condition interacts with identity, network reachability, and data sensitivity to form attack paths that static scanning never captured.
Operational reality compounds the problem. Development velocity introduces new services, dependencies, and identity relationships faster than periodic scans can assess. Security teams inherit findings without the context required to determine exploitability, while remediation queues grow detached from real risk.
The Shift to Continuous Exposure Management
Modern programs no longer ask which CVEs exist across the environment. Leaders now ask which exposures enable attackers to reach high-value assets. Attack path analysis traces how an internet-facing flaw in a development container, combined with broken authentication and permissive IAM roles, can lead directly to production data stores.
Risk evaluation has shifted from severity labels to probabilistic prediction. Exploit Prediction Scoring System (EPSS) scores estimate exploitation likelihood using threat intelligence, weaponization patterns such as MITRE, and attacker tooling. Internet exposure, identity privilege, data proximity, and compensating controls shape final risk decisions. Teams remediate a narrow subset of vulnerabilities that account for the vast majority of business risk rather than chasing every critical score.
Vulnerability management demands contextual analysis because modern breaches rely on chaining weaknesses. A single flaw rarely causes material damage. Effective programs surface and disrupt those chains before attackers can operationalize them.
Vulnerability Management Vs. Patch Management
In some respects, the vulnerability management process is akin to other security processes that IT organizations have practiced for decades, such as patch management. Like vulnerability management, patch management involves systematically finding and reacting to potential security risks (namely, unpatched software that attackers could exploit) before they become active problems.
But the vulnerability management process goes beyond patch management.
- Unpatched software is one way that vulnerabilities can be introduced into IT environments, but it's not the only way. Vulnerability management also addresses system misconfigurations, weak encryption standards, and insecure default settings — non-patchable flaws that often represent greater risk because they exist within authorized, up-to-date software.
- Whereas patch management typically involves the periodic installation of software patches, vulnerability management is a continuous process involving frequent and regular scans so teams can find and react to vulnerabilities in real time, whenever and wherever they appear.
- The vulnerability management process applies not just to assets (like applications) that can be patched but also to cloud services, infrastructure and other types of resources your IT team typically can't patch in the conventional sense.
Overview of Common Vulnerabilities and Exposures (CVEs)
When security researchers identify a vulnerability in publically-used software, they typically report it to a CVE database. CVE databases are lists of known vulnerabilities. They include details on what causes the vulnerability, how it can be exploited, how severe it is, and how to patch or update systems to mitigate the vulnerability.
Most CVE databases define this information using the Common Vulnerability Scoring System (CVSS), an open framework for sharing details about vulnerabilities and the severity they pose. By making vulnerability data accessible, CVEs and CVSS provide a critical resource that organizations can use to determine which vulnerabilities affect the systems or software they use. Additionally, it can tell teams how serious those vulnerabilities are and whether they can be exploited based on the specific configuration that the business uses.
The National Vulnerability Database and the MITRE CVE database are among the most popular public CVE databases. However, organizations can also maintain private or enhanced CVE data, which they may provide to other organizations as part of threat intelligence offerings.
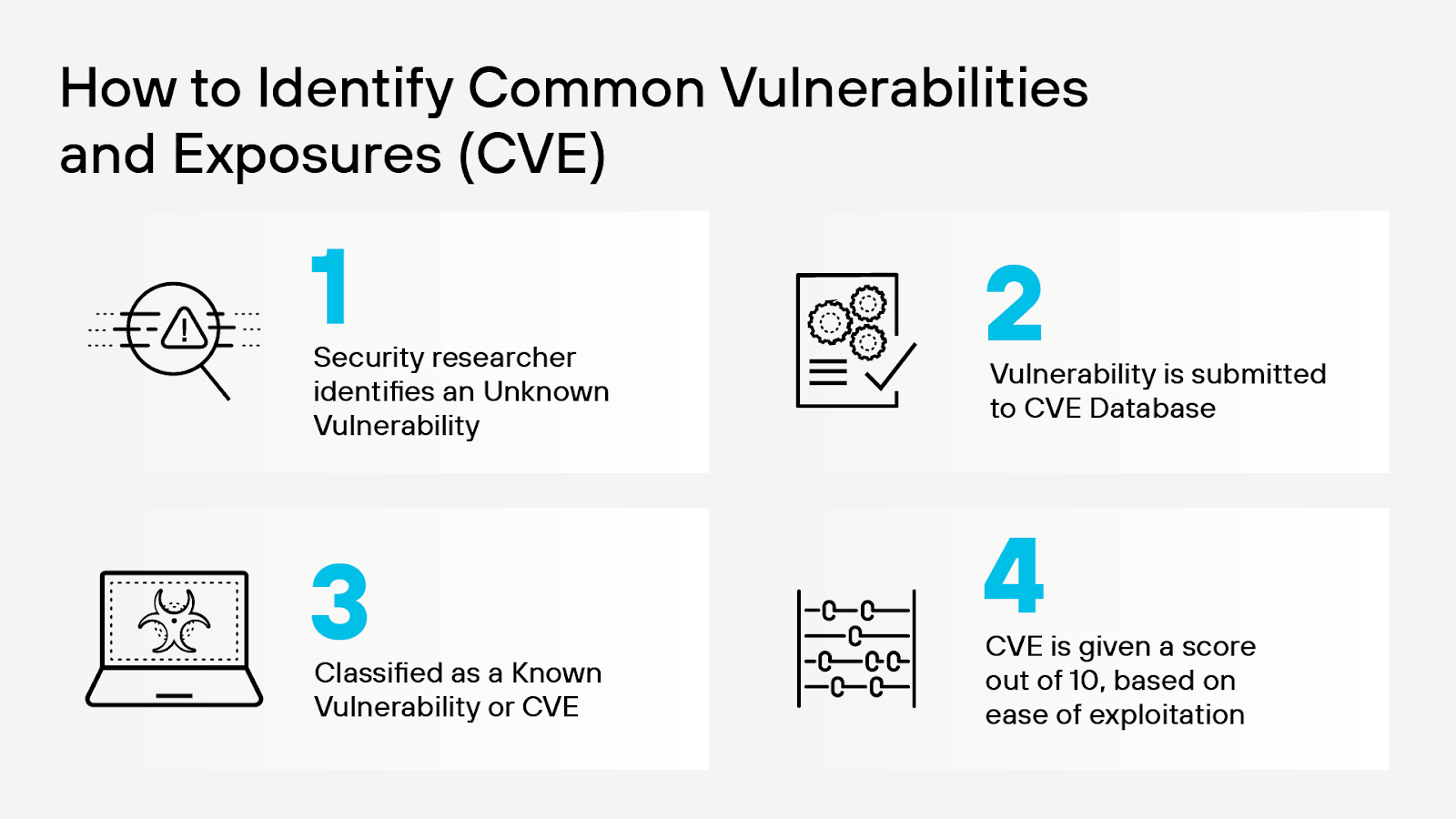
Figure 2: CVE identification process
An important limitation of CVEs is that they typically only list risks that affect publicly available software, such as open-source applications. Because software that an organization reserves for internal use is more difficult for third-party researchers to study, vulnerabilities within the software haven't necessarily been found or disclosed within CVE databases.
You shouldn’t, however, assume an application is free of vulnerabilities just because a CVE database says no known vulnerabilities have been found. The potential for unknown vulnerabilities to exist remains. Chances are, those that do are known to threat actors.
But security vulnerabilities, as mentioned above, come in many forms.
Broken Authentication
Broken authentication arises when access control logic, identity flows, or session management mechanisms fail to enforce intended trust boundaries. Weak credential handling, flawed token validation, insecure session lifecycles, or misconfigured authorization checks can allow malicious actors to impersonate users or escalate privileges beyond their assigned roles, exposing sensitive functions and data across the application.
Missing Authorization
A missing authorization vulnerability (CWE-862) occurs when an application fails to perform a check to verify that a user has the necessary permissions to access a resource or execute a function. While authentication confirms a user's identity, authorization ensures they stay within their assigned role. Without rigorous checks, attackers can exploit this gap to perform broken object level authorization (BOLA) attacks to access other users' private data, or broken function level authorization (BFLA) to invoke restricted administrative operations. These failures lead directly to privilege escalation and the exposure of sensitive system logic.
SQL Injection
SQL injection vulnerabilities (CWE-89) allow attackers to inject malicious queries into a database to manipulate data or exfiltrate information from it. SQL injection vulnerabilities typically occur due to lack of proper input validation within an application that interfaces with a database.
Cross-Site Scripting
A cross-site scripting vulnerability (CWE-79) allows attackers to run malicious scripts, most often affecting websites containing poorly written Javascript code. If attackers find the vulnerable code, they can trick the site into running scripts of their choosing, potentially giving them access to resources on the endpoints that connect to the website.
Cross-Site Request Forgery
Attackers can exploit cross-site request forgery vulnerabilities to cause users to inject malicious code into a website or application with which they're currently authenticated. They're similar to cross-site scripting vulnerabilities, with the major difference being that cross-site request forgery vulnerabilities center on impersonating authenticated users to perform malicious actions rather than executing malicious code through insecure Javascript.
Security Misconfigurations
Any type of security configuration mistake or oversight could trigger a vulnerability. Admins might inadvertently make sensitive data accessible via the internet due to a firewall configuration mistake, for example. Or they may forget to require multifactor authentication when configuring a new application deployment.
Vulnerability Management Vs. Vulnerability Assessment
Vulnerability assessment is a component of vulnerability management. When an individual vulnerability is discovered, it’s assessed to understand the level of risk it poses and to help determine how to remediate it.
Vulnerability assessment is important because not all vulnerabilities pose the same level of risk. For example, a vulnerability that can only be exploited by attackers who have physical access to a vulnerable system poses less risk than one that can be exploited over the network. Similarly, vulnerabilities that can only be exploited under specific configurations or environments pose less risk. Learning of restrictive circumstances via vulnerability assessment allows organizations to prioritize the most severe vulnerabilities to minimize their overall level of risk.
The Vulnerability Management Lifecycle
Vulnerability management operates in a system that connects discovery, risk evaluation, and remediation across rapidly changing environments. Each phase depends on the accuracy and discipline of the previous one, and maturity shows up in how consistently risk decisions translate into reduced exposure.
Asset Inventory
Asset inventory establishes the scope of accountability. Cloud environments demand real-time discovery mechanisms because workloads appear and disappear based on demand, development cycles, and infrastructure-as-code deployments. Agentless scanning technologies read runtime block storage and API metadata to maintain comprehensive inventories without performance overhead.
Discovery engines must catalog virtual machines, containers, Kubernetes clusters, serverless functions, managed databases, object storage, API gateways, and CI/CD pipelines. Shadow IT and unapproved SaaS integrations create blind spots where vulnerabilities accumulate undetected. Effective asset discovery pulls data from cloud provider APIs, container registries, service meshes, and identity providers to build complete topology maps.
Scanning
The vulnerability management cycle has shifted from quarterly scans to continuous assessment models. Traditional vulnerability scanners ran once per week or month, creating windows where newly disclosed CVEs went undetected. Modern vulnerability management solutions perform daily scans at a minimum, with some executing assessments every few hours.
Vulnerability scanning should occur across multiple layers simultaneously:
- Infrastructure layer scans evaluate VM operating systems, network configurations, and storage permissions.
- Application layer scans analyze code dependencies, library versions, and container image contents.
- Configuration layer scans assess IAM policies, encryption settings, and compliance posture.
Each layer requires specialized scanning techniques because a container vulnerability differs from a misconfigured security group. Equally important, scan results must map to active assets and current configurations. Findings disconnected from deployment context or runtime state create remediation friction and reduce confidence in security guidance.
Assessment
Assessment determines which findings merit action. Severity scores alone don’t capture exploitability or business impact. Modern assessment incorporates exposure to the internet, privilege context, identity trust relationships, proximity to sensitive data, and the presence of compensating controls.
Predictive signals such as EPSS scores, active exploitation intelligence, and attack path analysis refine prioritization. The goal isn’t to label every issue but to identify the weaknesses that meaningfully shorten an attacker’s path to critical systems.
Remediation
Remediation reduces exposure through patching, configuration changes, dependency upgrades, or architectural controls. Effective programs route actions to the teams that own the affected assets and align fixes with deployment workflows rather than rely on ad hoc tickets.
Not every vulnerability requires immediate patching. Network isolation, identity hardening, policy enforcement, or runtime protection can neutralize risk when patching timelines conflict with operational constraints. Decisions should favor measurable risk reduction over theoretical completeness.
Monitoring
Monitoring validates that risk stays reduced as environments evolve. New deployments, role changes, dependency updates, and configuration drift can reintroduce exposure without reintroducing the original vulnerability. Continuous validation confirms whether controls still block exploitation attempts under real conditions.
Runtime signals and configuration change tracking close the gap between intended security posture and actual behavior.
Reporting
Reporting translates technical activity into decision-relevant insight. Security leaders need visibility into exposure trends, remediation throughput, and recurring failure patterns. Executives need clarity on where risk concentrates and whether investments reduce meaningful attack paths.
Effective reporting emphasizes exposure reduction and remediation effectiveness rather than raw vulnerability counts, reinforcing accountability without encouraging superficial remediation.
Best Practices for Managing Cloud Workload Vulnerabilities
Enterprise security comes with no guarantee that you can catch and remediate all vulnerabilities before they turn into critical threats. You can, however, employ strategies to help you mitigate your risk of cyberattack.
Integrate Vulnerability Scanning into CI Processes
The earlier in the development lifecycle you catch vulnerabilities, the lower the risk that they’ll lead to breaches in production environments.
Integrate vulnerability scanning into your CI processes. Instead of waiting until workloads are in production, scan your hosts, containers, serverless functions and other resources in development and staging environments. Even if your configurations change between dev/staging and production, monitoring for vulnerabilities predeployment still maximizes your chances of preventing vulnerabilities from creeping into production.
Keep Scanning in Production
You should also perform continuous vulnerability monitoring after your workloads have been deployed to production. No amount of predeployment scanning is a substitute for checking for risks in production workloads.
Scan All Layers of Your Cloud Environment
A typical cloud workload includes multiple layers of configuration. Vulnerabilities can exist in each of them. If you deploy containers, you could have vulnerabilities in the container image. Vulnerabilities could also linger in the RBAC policies you configure in the container orchestrator. On top of this, policies that you configure using your cloud provider’s IAM framework could create risks for the containerized workload.
This is why it’s critical to scan all layers of your cloud workloads. Wherever data can exist, a vulnerability can also exist.
Use CVEs to Gain Vulnerability Context
As noted above, some vulnerabilities are more severe than others. But it’s not always obvious which ones require immediate attention.
Still, to make vulnerability alerts as actionable as possible, you need to know the severity level of each one. You can do this using CVE databases, which list known vulnerabilities and “score” them according to the amount of risk they pose.
By pairing vulnerability detection with CVE data, you get contextualized, actionable insights into cloud workload risks.
Setting Up a Vulnerability Management Framework
Although vulnerability management programs need to be tailored to the requirements of the organizations they serve, Gartner publishes a guidance framework that provides a starting point for establishing a vulnerability management program.
The key components of Gartner's framework include:
- Define the scope of the program: Businesses start their vulnerability management strategy by determining how many IT assets and vulnerability types they need to address.
- Define roles and responsibilities: Determining who does what and when is a critical component of vulnerability management. From frontline staff, like IT engineers, to CISOs and CTOs, everyone has a role to play in finding, reporting and managing vulnerabilities.
- Select vulnerability assessment tools: Businesses must decide which tools they'll use to find and assess vulnerabilities, as well as how vulnerability remediation will factor into their workflows and tooling.
- Create and refine policy SLAs: SLAs determine how quickly organizations will react to vulnerabilities and which level of active vulnerabilities they can tolerate. SLAs are an especially important resource to tailor to the business, since different organizations can tolerate different levels of risk.
- Identify asset context sources: Asset context sources provide complementary information, such as data about the role a system or application plays in the business, that can be critical for assessing vulnerabilities and their severity.
By addressing these guidelines, organizations can launch a program that empower them to find and react to vulnerabilities across all systems of concern.
Building a High-Performance Program
Successful vulnerability management programs require organizational transformation beyond deploying scanning tools. Executive commitment, cross-functional collaboration, and systematic improvement processes determine whether programs deliver measurable risk reduction or generate noise that teams ignore.
Establishing Security-Minded Culture
Vulnerability management fails when treated as a security team responsibility rather than an enterprise priority. Organizations experience cultural shifts after significant incidents expose the business impact of unmanaged vulnerabilities. Executive leadership must communicate that vulnerability remediation directly affects revenue protection, customer trust, and operational continuity.
Security-minded culture emerges when boards and C-suite executives allocate budget, adjust compensation structures, and remove organizational barriers preventing rapid remediation. Development teams need time dedicated to security work. Operations teams require authority to enforce patching schedules. Business units must accept temporary service disruptions for emergency updates.
Cross-Functional Alignment and SLA Discipline
Misaligned incentives across security, IT operations, development, and business stakeholders create friction where security teams identify vulnerabilities but lack the authority to mandate fixes.
SLA frameworks married to strict enforcement mechanisms ensure accountability. Critical vulnerabilities in internet-facing production systems might require remediation within 24 hours. High-severity internal vulnerabilities could allow for 7 days. Medium-severity findings might permit 30 days. SLA exceptions demand executive approval with documented risk acceptance.
Formal review processes, when teams miss SLA deadlines, identify systemic bottlenecks. Security and IT leadership regularly examine why remediation efforts stall and adjust processes, tooling, or staffing to eliminate obstacles.
Metrics Driving Continuous Improvement
Vulnerability management metrics must track business risk reduction rather than activity volume. Mean time to remediate measures how quickly teams close critical vulnerabilities after detection. Vulnerability age distribution reveals whether backlogs grow or shrink over time. Patch compliance rates show what percentage of assets run current software versions.
Attack surface metrics quantify internet-exposed assets, services accessible without authentication, and data stores lacking encryption. Organizations track how remediation efforts reduce these exposure metrics quarter over quarter. SLA compliance percentages highlight which teams consistently meet commitments versus those requiring additional support or resources.
Emergency Response Capabilities
Zero-day vulnerabilities and widespread exploitation campaigns demand emergency patching programs separate from routine vulnerability management workflows. Organizations prepare incident response plans specifically for vulnerability-driven crises, with predefined communication channels, decision authorities, and deployment procedures.
Emergency programs identify which systems require immediate patching versus those tolerating delayed updates. Pre-approved maintenance windows and rollback procedures enable rapid action when critical vulnerabilities emerge in widely-deployed software. Testing protocols balance speed against stability to prevent remediation efforts from causing operational disruptions worse than the vulnerabilities themselves.
Documentation of all vulnerability management phases enables continuous iterative improvement. Security teams assess each phase for inefficiencies, devise improvement strategies, and define metrics measuring progress. Programs evolve through regular retrospectives examining what worked, what failed, and how processes can improve for the next vulnerability management cycle.
Attacker Behavior-Based Remediation Prioritization
Threat and vulnerability management combines vulnerability data with active threat intelligence — EPSS probability scores, known exploited vulnerabilities catalogs, and campaign-specific intelligence about which CVEs threat actors currently weaponize — to prioritize remediation based on attacker behavior. When ransomware groups actively exploit a specific Apache vulnerability in their campaigns, threat and vulnerability management elevates that CVE above more severe flaws with no observed exploitation. Integration with threat intelligence feeds enables security teams to respond to emerging threats before widespread exploitation occurs.
Technology Stack and Integration Requirements
Vulnerability management platforms have evolved from fragmented scanning tools into security systems that unify detection, analysis, and response capabilities across cloud infrastructure.
Unified Cloud Security Platforms
Cloud-native application protection platforms (CNAPPs) serve as the central hub for vulnerability management workflows in distributed environments. Organizations deploy CNAPPs to consolidate cloud security posture management, cloud workload protection, and cloud infrastructure entitlement management into cohesive systems. Security teams using CNAPPs gain cross-layer visibility that connects infrastructure misconfigurations with workload vulnerabilities and identity risks within a single interface.
- Application security posture management (ASPM) enhances vulnerability management by providing a centralized view that correlates security data across the software lifecycle, allowing teams to prioritize the most critical risks based on business context and actual reachability.
- CSPMs continuously evaluate cloud infrastructure against security benchmarks and compliance frameworks while identifying configuration drift.
- Cloud workload protection platforms (CWPP) extend protection to compute resources by scanning operating systems, containers, and serverless code for exploitable weaknesses.
- CDR contributes to vulnerability management by providing runtime visibility and real-time detection of active exploits, allowing security teams to prioritize remediation based on which vulnerabilities attackers are currently targeting in the cloud environment.
When these standalone technologies operate within modern CNAPPs, vulnerability management becomes contextually aware of how risks cascade across architectural layers.
Deployment models matter significantly in cloud environments. Agentless architectures read cloud provider APIs and storage metadata to maintain asset inventories without installing software on target systems. Organizations achieve universal coverage across ephemeral workloads and managed services where agent installation proves impractical or impossible.
Development Pipeline Security Integration
The importance of ASPM can’t be understated. Vulnerability detection must occur during code commit and build phases to prevent flawed components from reaching production systems. Container registries integrated with vulnerability scanners reject images containing critical exploits before Kubernetes deployments begin. Development teams receive real-time notifications about vulnerable dependencies during pull request reviews rather than discovering problems weeks later in production.
Security gates within CI/CD platforms enforce policy-based deployment controls. Build pipelines query vulnerability management systems to verify that proposed deployments meet risk thresholds before releasing to staging or production environments. Automated policy enforcement prevents human error from introducing known vulnerabilities during rapid release cycles.
Dependency analysis tools examine application libraries and frameworks for CVEs cataloged in public databases. Package managers pulling from npm, PyPI, or Maven repositories introduce third-party code that security teams must evaluate. ASPM, integrated within CNAPP, tracks dependency chains to identify when upstream packages receive security updates requiring downstream application rebuilds.
Cross-Platform Intelligence Sharing
Security information and event management (SIEM) systems consume vulnerability data to enrich threat detection and incident response activities. When intrusion detection systems flag suspicious network traffic targeting specific ports, SIEM platforms correlate those events with vulnerability scan results showing which assets run services on those ports. Integrated intelligence enables security operations teams to assess whether detected threats target known weaknesses in their infrastructure.
Workflow automation platforms receive vulnerability findings and generate remediation tasks within project management systems. High-severity findings automatically create work items assigned to infrastructure teams with deadlines calculated from SLA policies. Closed-loop workflows update vulnerability management databases when remediation tasks are complete, triggering verification scans to confirm successful resolution.
Advanced Analytics and Path Modeling
Machine learning algorithms now analyze organizational environments to produce remediation guidance specific to deployed technologies and operational constraints. Generative models examine infrastructure-as-code repositories, deployment configurations, and historical remediation patterns to suggest fixes aligned with established practices.
Graph-based analysis maps potential compromise sequences by modeling how attackers exploit vulnerability chains to reach valuable targets. Platforms construct attack graphs showing how internet-exposed services with authentication weaknesses connect through overprivileged service accounts to backend databases. Risk scores adjust based on whether compensating controls interrupt potential attack paths or if clear routes exist from initial compromise to data exfiltration.
Vulnerability Management FAQs
The role of vulnerability management is to reduce the risk of security breaches and protect sensitive data by systematically identifying, assessing and addressing security vulnerabilities. Taking this proactive approach helps maintain a strong security posture, ensures compliance with industry standards and regulations, and minimizes potential damage from cyberthreats.
Every vulnerability management program should include regular vulnerability scanning, comprehensive risk assessment, timely remediation and ongoing monitoring. These four requirements ensure the continuous identification and mitigation of vulnerabilities, the prioritization of efforts based on risk, and the maintenance of a strong security posture to protect the organization's assets and data.
- Network vulnerabilities involve weaknesses in network infrastructure, protocols or configurations, enabling attackers to intercept, modify or disrupt data transmissions.
- Operating system vulnerabilities refer to flaws within the OS or its components, which can be exploited to gain unauthorized access, escalate privileges, or execute malicious code.
- Human vulnerabilities stem from human error or malicious actions, such as falling for phishing attacks, weak passwords or insider threats.
- Application vulnerabilities result from insecure coding practices and misconfigurations.
- Process vulnerabilities arise from inadequate security policies, procedures or compliance controls, leading to gaps in protection and increased risk of security breaches.
In cybersecurity, a threat refers to any potential malicious activity or event that aims to exploit vulnerabilities in systems, networks or applications, with the intent to compromise the confidentiality, integrity or availability of data and resources. Threats can originate from hackers, cybercriminals, nation-states or even insiders and can manifest in various forms, including malware, phishing attacks, denial-of-service attacks, ransomware or social engineering schemes.
Challenges of vulnerability management include:
- The constant emergence of new vulnerabilities
- Limited resources for addressing identified vulnerabilities
- Prioritizing remediation efforts
- Ensuring timely patching and configuration updates
- Maintaining visibility across a complex and evolving IT environment
- Overcoming human factors, such as resistance to change or lack of awareness.
Additionally, organizations must keep up with industry regulations and compliance requirements, adding another layer of complexity to the vulnerability management process.
The Common Vulnerability Scoring System (CVSS) is a widely adopted, standardized framework for assessing and rating the severity of security vulnerabilities in IT systems and cloud environments. CVSS provides a numerical score between 0 and 10, taking into account factors such as the ease of exploitation, impact on confidentiality, integrity, and availability, and the level of required user interaction. Higher scores indicate more severe vulnerabilities, enabling organizations to prioritize remediation efforts and allocate resources effectively.
A code security vulnerability refers to a weakness or flaw within the source code of a software application, resulting from programming errors, insecure coding practices or misconfigurations. Exploiting such vulnerabilities can enable attackers to compromise the application, gain unauthorized access to sensitive data, or perform malicious actions, potentially causing significant harm to the affected organization.
Vulnerabilities are scored for severity using standardized frameworks like CVSS, which considers factors such as the potential impact on confidentiality, integrity and availability, the complexity of exploitation, and the required level of user interaction. The resulting numerical score allows organizations to rank vulnerabilities based on their severity, helping to prioritize remediation efforts and allocate resources in a risk-based manner.
Organizations should scan all components of their IT environment for vulnerabilities, including network devices, servers, workstations, applications, databases and cloud infrastructure. Regular scanning of both internal and external systems, as well as the integration of vulnerability scanning into the software development lifecycle, ensures comprehensive coverage and helps to maintain a strong security posture.
Responsibility for vulnerability management typically falls on a combination of IT security teams, network administrators, system administrators and application developers. Effective vulnerability management requires collaboration and coordination across these teams, with individuals responsible for identifying, assessing and remediating vulnerabilities, as well as implementing security best practices and ensuring compliance with industry standards and regulations. In some organizations, a dedicated vulnerability management team or a chief information security officer (CISO) may oversee the entire process.
The most common type of vulnerability scan is the automated network vulnerability scan, which utilizes vulnerability scanning tools to identify and assess security weaknesses within an organization's network devices, servers and workstations. These scans typically cover a wide range of known vulnerabilities, including those related to outdated software, misconfigurations and insecure network protocols, helping organizations maintain a secure and compliant IT environment.
A vulnerability scan is performed using specialized tools that analyze IT systems for known security weaknesses, misconfigurations or outdated software. These tools typically use a combination of signature-based detection, heuristic analysis and manual testing to identify potential vulnerabilities. Scans can be conducted on a scheduled basis, after significant changes to the environment, or on-demand, with results providing detailed information on identified vulnerabilities and recommendations for remediation.
EPSS calculates the probability that a vulnerability will be exploited within the next 30 days based on threat intelligence, attacker behavior patterns, and weaponization trends. Unlike CVSS scores that measure theoretical severity, EPSS provides data-driven exploitation likelihood percentages, enabling security teams to prioritize vulnerabilities that threat actors are actively targeting over those with higher severity but lower exploitation probability.
A CVE (Common Vulnerabilities and Exposures) vulnerability scan is a process that uses a vulnerability scanning tool to identify known security vulnerabilities within IT systems, based on the CVE database. The CVE database is a publicly accessible, standardized repository of known security vulnerabilities, maintained by the MITRE Corporation. CVE vulnerability scans help organizations detect and address known vulnerabilities in their systems, reducing the risk of security breaches and improving overall security posture.
Vulnerability scanning NIST refers to the process of identifying security vulnerabilities in IT systems, following the guidelines and recommendations provided by the National Institute of Standards and Technology (NIST). NIST offers best practices, such as those found in NIST Special Publication 800-53 and 800-115, to help organizations implement effective vulnerability scanning processes, maintain a strong security posture and ensure compliance with federal regulations and industry standards.