- What Is Cloud Native?
- What Is Threat Modeling?
- CSP-Built Security Vs. Cloud-Agnostic Security
- What Are Microservices?
- What Is Cloud-Native Security?
- What Is CSPM? | Cloud Security Posture Management Explained
- What Is Cloud Network Security?
- What Is Microsegmentation?
-
Core Tenets of a Cloud Native Security Platform (CNSP)
- What Is a Cloud Native Security Platform?
- CSPM Tools: How to Evaluate and Select the Best Option
- What is Platform as a Service (PaaS)?
-
What Is Serverless Security?
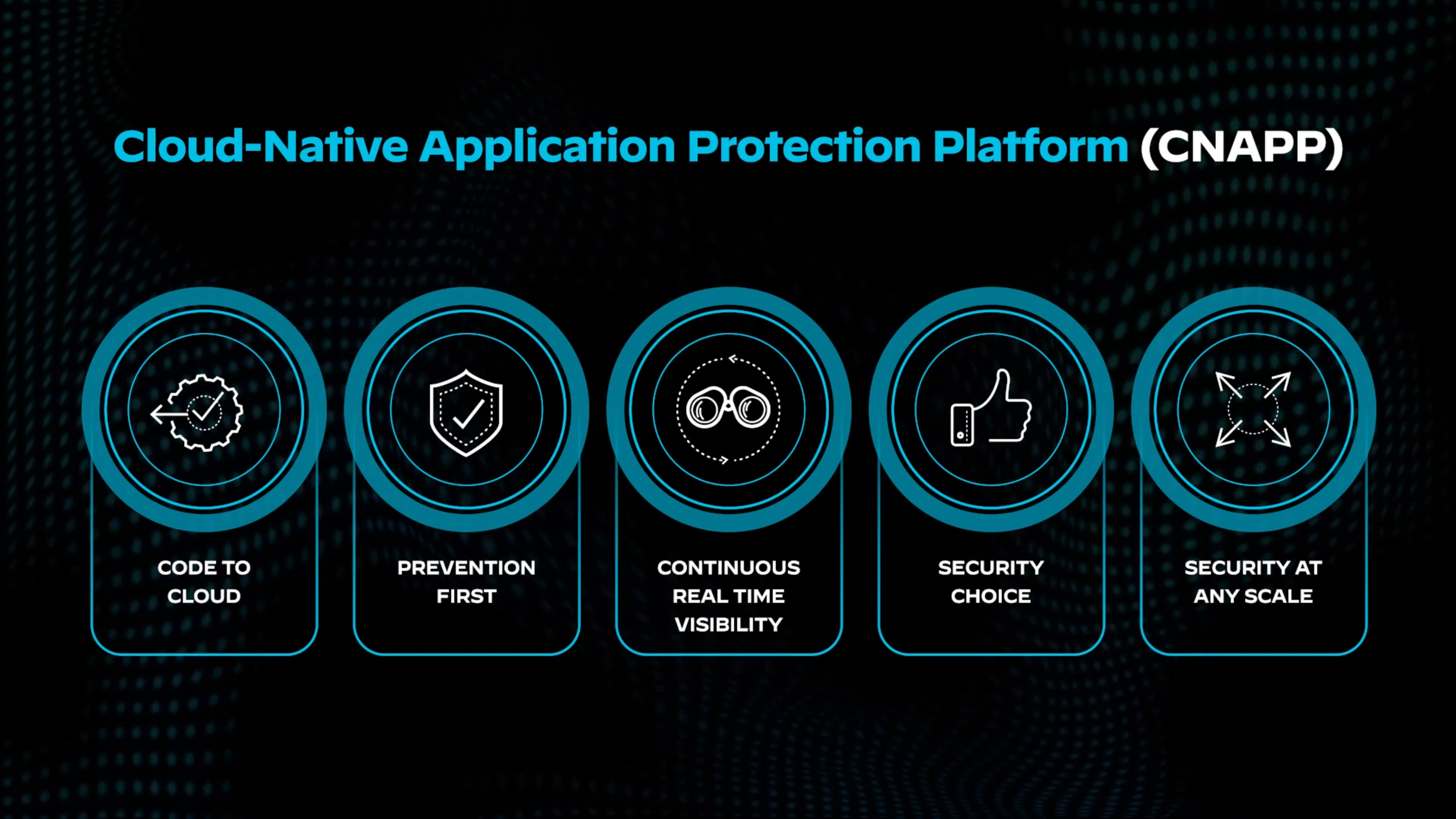
What Is CNAPP?
A cloud-native application protection platform (CNAPP) secures every phase of cloud-native applications, from development to production. Traditional tools manage isolated tasks, but CNAPPs unify security and compliance into a single platform. Consolidation improves visibility, manages configurations, and protects both development and production environments.
CNAPPs monitor operations continuously, regardless of the cloud provider or architecture. By integrating security into every step, they ensure development, operations, and security teams collaborate efficiently to address risks throughout the lifecycle of modern applications.
CNAPP Explained
A cloud-native application protection platform (CNAPP) is a unified security solution designed to address the entire lifecycle of cloud-native applications — from development through to production. Unlike traditional security tools that operate in silos, CNAPPs integrate a range of security and compliance capabilities within a single platform. The consolidated approach helps organizations gain visibility into risks, manage configurations, and ensure secure development while detecting runtime threats.
CNAPPs streamline security operations by providing continuous monitoring and governance, regardless of the cloud service provider or architecture in use. The platform bridges the gap between development, operations, and security, fostering collaboration and ensuring that risks are addressed efficiently throughout the lifecycle of modern cloud-native applications.
At their core, CNAPPs offer proactive protection through features such as artifact scanning, cloud security posture management (CSPM), and infrastructure as code (IaC) security. They also provide reactive security by offering runtime workload protection and attack path analysis. Combining proactive and reactive capabilities ensures that applications remain secure, even as they evolve, integrating with CI/CD pipelines, cloud platforms, and microservices architectures.
Evolution of Cloud Security Leading to CNAPPs
The adoption of cloud-native technologies transformed how applications are developed and deployed, shifting operational responsibilities toward developers and cloud architects. Traditional security tools designed for monolithic applications failed to keep pace with the agility of modern development practices. As organizations embraced containers, serverless architectures, and infrastructure as code, the need arose for security solutions capable of scaling alongside dynamic environments.
Initially, specialized tools like CSPM and cloud workload protection platforms (CWPP) emerged to address individual aspects of cloud security. Managing multiple tools, however, created operational silos, and silos resulted in fragmented risk assessments, inconsistent policies, and limited collaboration between teams. Developers, security operations, and cloud architects often operated independently, using disconnected systems that lacked shared visibility and context.
Fragmentation, in fact, fueled the demand for an integrated solution. Organizations needed security that could operate seamlessly across development and runtime environments while supporting multicloud and hybrid deployments. As security responsibilities shifted left, it became important to empower developers to address risks proactively.
CNAPPs emerged as a direct response to these challenges, consolidating disparate tools and providing a unified platform that could deliver both development and operational security.
The Need for Integrated Security in Cloud-Native Environments
Cloud-native environments present unique challenges, including rapid development cycles, ephemeral workloads, and complex multicloud architectures. With applications often composed of multiple microservices and relying heavily on APIs, the attack surface has expanded. Comprehensive security suddenly became more challenging to achieve.
CNAPPs embed security into DevOps workflows, offering visibility from code to runtime. They automate the detection of vulnerabilities, misconfigurations, and compliance issues, allowing teams to act early. Security becomes part of the process, not an obstacle, ensuring issues are resolved before deployment.
The integrated approach supports a shift-left mindset, reducing costly remediation later. CNAPPs also maintain continuous governance, ensuring secure operations even as workloads and infrastructure evolve. By unifying security and operational tools, they help organizations stay secure and agile in dynamic cloud-native environments.
Key Components of a CNAPP
Cloud-native application protection platforms provide a comprehensive, unified approach to security by combining traditionally separate security tools into a single platform. Consolidation offers visibility, protection, and governance throughout the application lifecycle — from development to runtime. Each component addresses critical areas of cloud-native security. Integration results in stronger security, reduced operational overhead, and the ability to innovate without compromising on safety.
Cloud Security Posture Management (CSPM)
CSPM plays a pivotal role in ensuring the security of cloud infrastructure by continuously monitoring and validating configurations.
- Continuous Monitoring of Cloud Infrastructure: With cloud environments evolving rapidly, misconfigurations can occur frequently, introducing vulnerabilities. CSPM ensures organizations have real-time insight into the configuration of their cloud assets, identifying risks before they can be exploited.
- Compliance and Misconfiguration Checks: CSPM assesses configurations against industry benchmarks and regulatory frameworks such as CIS, NIST, and HIPAA. Compliance is critical for meeting regulatory requirements and avoiding penalties. Misconfigurations, like open storage buckets or excessive permissions, are a common cause of cloud breaches.
- Automated Remediation Capabilities: Manually addressing misconfigurations across dynamic cloud environments is labor-intensive. CSPM automates remediation or provides actionable recommendations, ensuring risks are mitigated quickly and consistently.
Why CSPM Is Essential
CSPM reduces the cloud attack surface by continuously checking for common vulnerabilities and security gaps. It ensures cloud infrastructure remains secure and compliant, helping organizations avoid costly breaches and regulatory fines.
Cloud Workload Protection Platform (CWPP)
CWPP provides runtime security for workloads deployed across VMs, containers, and serverless functions.
- Runtime Protection for Containers, VMs, and Serverless Functions: As workloads shift from traditional data centers to cloud environments, they become more ephemeral and dynamic. CWPP ensures real-time visibility and protection across these workloads, even as they scale up and down.
- Threat Detection and Response: CWPP monitors for abnormal behavior or indicators of compromise, enabling rapid responses to mitigate attacks before they escalate.
- Vulnerability Management in Running Workloads: CWPP identifies and prioritizes vulnerabilities within workloads, allowing security teams to apply patches or mitigation techniques without disrupting operations.
Why CWPP Is Essential
CWPP ensures that workloads are protected during runtime, the most vulnerable stage in cloud environments. Without CWPP, organizations risk leaving workloads exposed to real-time attacks, such as malware or ransomware targeting containers and virtual machines.
Cloud Infrastructure Entitlement Management (CIEM)
CIEM focuses on managing access and permissions across cloud services, which is critical for reducing insider threats and unauthorized access.
- Identity and Access Management in the Cloud: CIEM provides visibility into both human and machine identities across cloud platforms, ensuring only the right entities access sensitive resources.
- Privilege and Permission Analysis: Many cloud environments suffer from "permission creep," where users accumulate unnecessary privileges over time. CIEM identifies excessive permissions, ensuring minimal access for each role.
- Least Privilege Enforcement: CIEM enforces the principle of least privilege, ensuring that users and services only have access to what is necessary for their roles.
Why CIEM Is Essential
Poorly managed identities and excessive permissions are among the leading causes of cloud breaches. CIEM ensures organizations minimize the attack surface by controlling access and reducing the risk of privilege escalation attacks.
Data Security Posture Management (DSPM)
DSPM secures sensitive data in cloud environments by continuously monitoring and managing risks across structured and unstructured datastores.
- Cloud Data Risk Visibility: DSPM identifies where sensitive data resides and how it’s accessed, helping organizations manage risks associated with unauthorized access or data exposure.
- Compliance Monitoring: It ensures that data security aligns with regulatory frameworks such as GDPR, PCI DSS, and HIPAA, reducing the risk of fines and legal repercussions.
- Automated Risk Mitigation: DSPM provides automated remediation and access controls to prevent unauthorized data exposure.
Why DSPM Is Essential
With the increasing reliance on cloud-based data storage, data breaches are a constant threat. DSPM helps organizations protect sensitive data, manage compliance, and reduce the likelihood of costly data leaks.
Kubernetes Security Posture Management (KSPM)
KSPM provides specialized security for Kubernetes, which is foundational to modern microservice architectures.
- Kubernetes Configuration Auditing: Misconfigured clusters are a common attack vector. KSPM audits these configurations to identify risks and vulnerabilities.
- Cluster Security Monitoring: KSPM monitors clusters to detect unusual activity, ensuring that workloads remain secure in production.
- Policy Enforcement and Drift Detection: It enforces security policies across Kubernetes clusters and identifies drift from expected configurations, ensuring consistency and reducing risk.
Why KSPM Is Essential
Kubernetes has become the backbone of cloud-native infrastructure, but its complexity can introduce vulnerabilities. KSPM ensures these environments remain secure, minimizing the risk of attacks targeting orchestration layers.
AI Security Posture Management (AI-SPM)
AI-SPM safeguards AI models and infrastructure by monitoring, assessing, and managing risks. As organizations deploy AI applications, challenges arise around data integrity, model manipulation, and misuse of AI. AI-SPM ensures secure, compliant, and resilient AI deployments.
- Model Integrity: Detects vulnerabilities like model poisoning, adversarial attacks, or tampering, ensuring models perform securely throughout their lifecycle.
- Data Security: Protects sensitive data used for AI, maintaining privacy and compliance with regulations such as GDPR and HIPAA.
- Continuous Risk Monitoring: Identifies risks like improper access, bias, and unintended AI behavior, ensuring safe operation and early mitigation.
Why AI-SPM Matters
Traditional security tools can’t fully address AI-specific risks. AI-SPM ensures models, data, and pipelines remain secure, mitigating threats and supporting compliance while also reducing risks and strengthening decision-making.
DevSecOps Integration
DevSecOps focuses on embedding security into development processes, ensuring risks are addressed early in the application lifecycle.
- Shift-Left Security Practices: DevSecOps promotes the idea of identifying security risks during development, rather than waiting until deployment, saving time and cost.
- Integration with CI/CD Pipelines: CNAPPs integrate directly with CI/CD tools, automating security scans during code development and delivery, without slowing down the pipeline.
- Infrastructure as Code (IaC) Scanning: CNAPPs scan IaC templates to detect vulnerabilities or misconfigurations, ensuring that secure infrastructure is deployed.
- Software Composition Analysis: By analyzing open-source dependencies and third-party libraries, CNAPPs help developers understand and manage risks within the software supply chain.
Why DevSecOps Integration Is Important
Early identification of risks minimizes the need for late-stage fixes and reduces deployment delays. DevSecOps ensures security becomes part of the development culture, preventing vulnerabilities from entering production.
API Security
APIs serve as the connective tissue in cloud-native environments, but they also introduce new attack surfaces.
- API Discovery and Inventory: CNAPPs automatically discover and catalog APIs to ensure visibility into all exposed endpoints.
- API Threat Protection: They monitor for API-specific threats, such as injection attacks or unauthorized access, and block malicious requests in real time.
- API Governance and Compliance: CNAPPs enforce security policies and governance frameworks for APIs, ensuring they align with organizational compliance requirements.
Why API Security Is Essential
Attackers increasingly target APIs because they expose critical services. Without effective API security, organizations risk data breaches and service disruptions caused by compromised APIs.
CNAPP Architecture and Functionality
The architecture of CNAPPs is designed to unify multiple security functions into a single, integrated platform. Facilitating seamless collaboration across security, operations, and development teams ensures that risks are identified, prioritized, and mitigated across the entire application lifecycle.
Unified Dashboard and Reporting
A unified dashboard serves as the central hub for visibility and management, offering real-time insights across cloud environments and helping stakeholders prioritize actions.
- Centralized Visibility Across Cloud Environments: With CNAPPs, organizations gain a consolidated view of all their assets, workloads, APIs, and configurations across public, private, and hybrid cloud environments. Comprehensive visibility reduces blind spots and ensures that security teams can monitor the entire attack surface from one place.
- Risk Prioritization and Scoring: CNAPP dashboards leverage analytics to prioritize risks based on severity, business impact, and the likelihood of exploitation. By ranking risks, the platform ensures teams focus on the most critical issues first, preventing them from becoming overwhelmed by low-priority alerts.
- Compliance Reporting: CNAPPs offer built-in compliance reporting, automating assessments against industry frameworks (e.g., PCI DSS, GDPR, HIPAA) and generating reports for audits. The feature helps organizations demonstrate compliance and easily track remediation efforts over time.
Why a Unified Dashboard Is Important
A unified dashboard reduces operational complexity by consolidating multiple tools and providing a single source of truth. It improves decision-making by ensuring teams have the right information at their fingertips and can act swiftly on high-priority risks.
Data Collection and Analysis
CNAPPs collect and analyze data from multiple sources to identify vulnerabilities, misconfigurations, and active threats in real-time. The architecture supports both agent-based and agentless methods of data collection, ensuring flexibility for different environments.
- Agentless vs. Agent-Based Approaches: CNAPPs offer agentless scanning to reduce deployment overhead by accessing data directly from cloud APIs and logs. They also provide agent-based options for deeper visibility into runtime environments, such as containers or virtual machines, where continuous monitoring is critical.
- Machine Learning and AI for Threat Detection: Advanced CNAPPs leverage machine learning (ML) and artificial intelligence (AI) to detect anomalies and identify emerging threats. By analyzing behavioral patterns, the system can distinguish between normal activities and potential attacks, improving detection accuracy.
- Real-Time Monitoring and Alerting: The platform continuously monitors workloads and cloud services, issuing alerts the moment it detects unusual activity or deviations from policies, which allows teams to respond promptly.
Why Data Collection and Analysis Is Important
Effective data collection and analysis are essential for early threat detection and fast response. The combination of agent-based and agentless options ensures the platform can adapt to diverse environments, while AI and ML enhance accuracy, reducing false positives and operational burden.
Policy Management and Enforcement
CNAPPs enable organizations to create, manage, and enforce security policies across their entire cloud infrastructure. A policy-driven approach ensures consistent security practices, even as cloud environments evolve and scale.
- Custom Policy Creation: The platform allows security teams to create custom policies tailored to their organization’s unique requirements. These policies can cover everything from access controls to workload configurations, ensuring that security practices align with business goals.
- Policy-Driven Automation: CNAPPs support policy-based automation, allowing routine security tasks — such as patching, remediation, or configuration changes — to occur without manual intervention. Automation reduces human error and ensures timely action on security issues.
- Cross-Cloud Policy Consistency: A key benefit of CNAPPs is the ability to enforce consistent policies across multiple cloud providers. Without this, organizations will struggle to implement uniform security standards across platforms (e.g., AWS, Azure, GCP).
Why Policy Management and Enforcement Is Important
Policy management ensures that security practices are proactive, not reactive. Consistent enforcement across clouds reduces the likelihood of configuration drift or policy gaps, while automation accelerates responses to security events, keeping environments secure without manual oversight.
CNAPP Implementation Strategies
Implementing a CNAPP requires thoughtful planning and execution to ensure it aligns with the organization’s security goals and integrates smoothly within existing workflows. A successful CNAPP implementation enables streamlined security operations, improved visibility, and proactive risk management across cloud environments.
Assessment and Planning
The first phase of CNAPP implementation focuses on evaluating the current cloud environment, identifying security gaps, and defining a roadmap for execution.
- Cloud Environment Evaluation: Organizations must assess their cloud infrastructure, including the providers they use, the workloads running in the cloud, and the tools already in place. Evaluation provides a baseline of the environment's complexity, key assets, and data flows.
- Security Gaps Identification: An in-depth security audit identifies vulnerabilities, misconfigurations, excessive permissions, and blind spots across the cloud ecosystem. Gap analysis helps determine the areas where CNAPP can provide the most value, whether in misconfiguration management, API security, or workload protection.
- Roadmap Development: With insights from the evaluation, security leaders create a step-by-step implementation roadmap. The plan includes priorities for each component (e.g., CSPM, CWPP) and aligns deployment timelines with business objectives, ensuring minimal disruption during the rollout.
Why Assessment and Planning Is Important
A thorough assessment ensures that CNAPP implementation addresses the most critical risks and aligns with the organization’s strategic goals. This phase lays the foundation for a smooth deployment by identifying what needs protection and where the biggest vulnerabilities lie.
Deployment and Integration
The deployment phase involves configuring the CNAPP across cloud environments and integrating it with the organization’s existing tools and processes.
- Multicloud Implementation Considerations: Many organizations operate across multiple cloud providers, each with different configurations and security requirements. CNAPPs must be implemented in a way that ensures consistent protection across all cloud platforms, without introducing complexity or conflicts.
- Integration with Existing Security Tools: To maximize value, CNAPPs must integrate seamlessly with existing tools, such as security information and event management (SIEM) platforms, endpoint detection and response (EDR) tools, and identity management systems. Integration allows for data sharing, coordinated threat responses, and a unified security strategy.
- Performance Optimization: CNAPP deployment must balance security with performance. Organizations need to configure agent-based monitoring carefully to avoid resource bottlenecks and optimize agentless scanning to ensure real-time visibility without compromising cloud performance.
Why Deployment and Integration Is Important
Deployment and integration are critical to ensuring that CNAPPs operate efficiently within complex cloud environments. A well-integrated solution reduces operational silos, strengthens collaboration between teams, and ensures smooth cloud operations without performance degradation.
Continuous Improvement
Security in cloud-native environments requires ongoing optimization to adapt to new risks and evolving cloud landscapes.
- Regular Security Posture Reviews: Continuous improvement relies on regular assessments of the organization’s cloud security posture. CNAPPs help organizations track metrics such as the number of misconfigurations, open vulnerabilities, and compliance gaps over time, enabling continuous monitoring and adjustments.
- Threat Intelligence Incorporation: CNAPPs become more effective when they integrate with external threat intelligence feeds. Integration allows the platform to detect emerging threats and automatically adjust policies to respond to new vulnerabilities, keeping the environment resilient against the latest attacks.
- Adapting to Evolving Cloud Landscapes: Cloud environments are dynamic, with new services, architectures, and workloads introduced regularly. Organizations must ensure that their CNAPP evolves alongside these changes, scaling with new workloads and adapting security policies to reflect emerging risks, such as those associated with AI-based services or API expansion.
Why Continuous Improvement Is Key
Continuous improvement ensures that CNAPPs remain effective over time, addressing new threats and adapting to changing cloud architectures. Without regular reviews and threat intelligence updates, security gaps can emerge, exposing organizations to evolving risks.
CNAPP Benefits
Cloud-native application protection platforms offer transformative benefits by consolidating security operations into a single, integrated platform, ultimately empowering organizations to align security with business goals, improve operational efficiency and enable innovation without sacrificing safety.
Efficient Management and Operations
Managing cloud security through multiple, disconnected tools often leads to operational silos and inefficiencies. CNAPPs solve this problem by integrating security functions such as CSPM and CWPP into a cohesive framework. Consolidation streamlines workflows, reduces complexity, and enables security, development, and operations teams to collaborate more effectively.
By automating routine tasks like vulnerability scanning and compliance checks, CNAPPs free up resources, allowing teams to focus on higher-value activities. Organizations benefit from reduced overhead and faster responses to security incidents, creating a more agile security posture.
Consistent Security Policies Across Clouds
In today’s multicloud environments, ensuring consistent security policies is a significant challenge due to the unique configurations of each platform. CNAPPs solve this issue by enforcing uniform policies across multiple cloud platforms, reducing the risk of inconsistencies. With policy-driven automation, CNAPPs ensure that security practices are applied consistently, even as cloud services evolve. The approach prevents configuration drift, which can leave resources vulnerable to attack. Cross-cloud policy consistency not only simplifies management but also reduces human error, helping organizations maintain a robust security posture.
Enhanced Compliance Management
Regulatory compliance remains a top priority for organizations across industries, and CNAPPs play a crucial role in meeting these requirements. Traditional compliance processes can be time-consuming and prone to human error. CNAPPs automate compliance checks by continuously monitoring cloud configurations and assessing them against relevant standards.
With prebuilt reporting templates, CNAPPs simplify audits and reduce the burden on security teams. These platforms also provide real-time alerts when compliance issues arise, allowing organizations to address them promptly. Proactive compliance management ensures that organizations stay ahead of regulatory requirements, avoiding costly penalties and reputational damage.
Better Risk Prioritization
Cloud-native environments generate an overwhelming number of security alerts, making it difficult for teams to focus on the most critical issues. CNAPPs use contextual risk scoring to prioritize vulnerabilities based on factors such as severity, business impact, and the likelihood of exploitation. This helps security teams cut through the noise and focus on what matters most.
CNAPPs also consolidate alerts from multiple tools, reducing alert fatigue and streamlining remediation efforts. By identifying high-priority risks early in the development lifecycle, CNAPPs enable organizations to address vulnerabilities before they reach production, reducing the need for disruptive fixes later on.
Full Visibility and Context Across Cloud Environments
Lack of visibility across distributed workloads, APIs, and cloud services poses the most significant challenges in securing cloud-native environments. CNAPPs offer end-to-end visibility, from code development to runtime operations, ensuring that security teams have eyes on the entire ecosystem.
Visibility extends to APIs, containers, and identities, allowing teams to monitor every component and detect risks in real time. The integration of data from multiple sources provides context for security events, making it easier to understand the root cause of issues and plan effective remediation. By eliminating blind spots, CNAPPs enhance security while enabling more informed decision-making.
Scalable and Future-Proof Security
As organizations expand their use of cloud services, security tools must keep pace with evolving workloads and architectures. CNAPPs are designed to scale with dynamic cloud environments, providing flexible monitoring options, including agent-based and agentless methods. Adaptability is imperative, as it ensures that security remains effective even as organizations adopt new technologies like serverless computing, microservices, and AI-driven services.
CNAPPs also integrate seamlessly with DevSecOps practices, embedding security into CI/CD pipelines and promoting a shift-left approach to risk management. As cloud landscapes evolve, CNAPPs remain future-proof by supporting emerging architectures and scaling alongside the business.
Faster Response to Threats
In cloud-native environments, the speed at which threats emerge requires equally fast responses. CNAPPs enable organizations to detect, contain, and remediate threats in real time, reducing the window of exposure. Automated threat detection and response capabilities streamline incident handling, minimizing the impact of security breaches. CNAPPs also integrate with external threat intelligence feeds, ensuring that the platform remains up to date with the latest attack vectors. By accelerating response times, CNAPPs help organizations limit damage and maintain business continuity, even in the face of sophisticated attacks.
The AI-Enhanced CNAPP
AI and machine learning have become essential in enhancing the effectiveness of CNAPPs. Cloud-native environments are dynamic, with workloads, configurations, and APIs continuously changing. Dynamism and complexity make manual security management insufficient for detecting subtle threats or predicting potential vulnerabilities. AI-enhanced CNAPPs address these challenges by using advanced analytics, automation, and predictive capabilities to stay ahead of evolving risks.
Related Article: Tame Complexity, Turbocharge Security: Prisma Cloud Copilot
Adaptive Threat Detection and Anomaly Detection
AI-powered CNAPPs continuously monitor cloud environments to detect suspicious activity. Traditional rule-based detection methods can miss unknown or emerging threats, especially in dynamic cloud settings. AI solves the limitation by identifying patterns and deviations that signal potential threats.
- Anomaly Detection: AI models learn the normal behavior of workloads, containers, and APIs over time. When deviations occur — such as unusual API calls or unexpected configuration changes — AI detects these anomalies, triggering alerts for further investigation.
- Behavioral Analytics: Instead of relying on static rules, AI analyzes behavioral data to identify evolving attack techniques, such as privilege escalation or lateral movement, before they cause damage.
- Improved Detection Accuracy: With AI, CNAPPs minimize false positives by refining detection models based on historical data, ensuring that alerts are meaningful and actionable.
AI’s ability to identify threats in real-time, even those that don’t match known attack signatures, ensures that organizations can respond proactively to advanced and zero-day threats.
Predictive Analytics and Risk Forecasting
AI enhances CNAPPs by offering predictive insights into potential security risks. By analyzing historical trends, cloud usage patterns, and vulnerability data, AI models forecast where risks are likely to arise.
- Proactive Vulnerability Management: AI identifies vulnerabilities based on historical patterns, giving security teams the opportunity to address issues before they’re exploited. For example, if certain configurations have been linked to breaches in the past, AI flags similar setups as high risk.
- Attack Path Prediction: AI models simulate potential attack paths, helping organizations understand how a vulnerability or misconfiguration could be exploited to reach sensitive resources. This insight allows teams to proactively block attack vectors.
- Dynamic Risk Scoring: AI adjusts risk scores dynamically based on real-time changes in the cloud environment, ensuring that the most critical threats are always prioritized.
Predictive analytics ensure that security teams stay ahead of potential risks, reducing the time and effort needed to identify and address vulnerabilities.
Intelligent Automation and Remediation
AI enables CNAPPs to automate not just detection but also the response to security incidents. AI-driven automation reduces the burden on security teams, allowing them to focus on more strategic initiatives.
- Automated Policy Enforcement: AI enforces security policies across cloud environments automatically, ensuring that configurations remain compliant even as workloads evolve.
- Self-Healing Systems: CNAPPs use AI to implement automated remediation, fixing misconfigurations and vulnerabilities without manual intervention. For instance, AI can reconfigure settings or disable access if it detects policy violations or suspicious behavior.
- Intelligent Playbooks: AI optimizes security workflows by learning from past incidents. It suggests automated responses based on the most effective remediation strategies previously used, improving efficiency over time.
With intelligent automation, AI-enhanced CNAPPs minimize human error and accelerate incident response, keeping environments secure with minimal disruption.
Contextual Insights for Security Teams
AI enhances the contextual intelligence of CNAPPs, helping security teams understand the relationships between risks, vulnerabilities, and business-critical resources.
- Advanced Correlation Capabilities: AI correlates data from multiple sources — such as APIs, workloads, and cloud services — into a unified threat narrative, giving teams deeper insights into complex security events.
- Root Cause Analysis: AI identifies the root cause of issues, enabling teams to address underlying vulnerabilities instead of just treating symptoms. Addressing root causes eliminates repetitive security incidents.
- Prioritized Recommendations: AI provides actionable recommendations, prioritizing remediation steps based on business impact and the severity of the threat.
These contextual insights empower teams to make faster, more informed decisions, improving the overall security posture of the organization.
Enhanced Compliance Monitoring and Governance
AI plays a crucial role in automating compliance management and ensuring continuous governance across cloud environments.
- Continuous Compliance Monitoring: AI scans configurations and workloads for compliance violations in real time, reducing the risk of noncompliance.
- Policy Optimization: AI refines security policies by identifying patterns that lead to violations, suggesting improvements to prevent future compliance gaps.
- Automated Reporting: AI streamlines the creation of audit reports, ensuring that organizations can demonstrate compliance quickly and efficiently during audits.
AI ensures that compliance is maintained without adding overhead to security teams, enabling faster audits and reducing the risk of penalties.
Adapting to Evolving Threat Landscapes
Cloud-native environments are constantly changing, and attackers continue to develop new techniques. AI ensures that CNAPPs evolve alongside these changes.
- Continuous Learning Models: AI algorithms learn from new threats and adapt their detection capabilities accordingly, staying ahead of attackers.
- Integration with Threat Intelligence Feeds: AI-enhanced CNAPPs incorporate external threat intelligence feeds to improve detection and stay current with the latest attack vectors.
- Agile Security Practices: AI helps organizations adjust security strategies on the fly, enabling them to respond to evolving risks without disrupting cloud operations.
The ability to adapt ensures that CNAPPs remain effective, even as cloud environments grow more complex and the threat landscape evolves.
What’s Next for CNAPP?
The future of CNAPPs lies in their ability to evolve alongside cloud environments and security needs. As organizations embrace more complex architectures, emerging technologies, and stricter security frameworks, CNAPPs must integrate new capabilities to remain relevant. Two major developments on the horizon are the deeper integration of extended detection and response (XDR) and alignment with Zero Trust architecture.
Extended Detection and Response (XDR) Integration
The convergence of CNAPP with XDR is a natural evolution, as both aim to unify and streamline threat detection and response across environments. XDR aggregates data from multiple sources — such as endpoints, network activity, and cloud workloads — providing a centralized view of security events. CNAPP platforms complement XDR by offering deep insights into cloud-native risks, configurations, and vulnerabilities.
Integrating CNAPP with XDR enables organizations to detect threats holistically, correlating activity across cloud environments, on-premises systems, and user devices. Integration improves the accuracy of threat detection by providing greater context, such as linking a misconfiguration in the cloud to suspicious behavior on an endpoint. With both platforms working in tandem, incident response becomes faster and more effective, as teams can identify the root cause of incidents and act with precision.
XDR integration also reduces the burden on security operations centers (SOCs) by centralizing alerts and offering actionable insights. With the complexity of cloud-native environments growing, this kind of unified visibility will be critical to maintaining an agile and efficient security posture.
Zero Trust Architecture Alignment
As Zero Trust becomes the guiding principle for modern security frameworks, CNAPPs are increasingly aligning with its core tenets. Zero Trust assumes that no user, workload, or system can be trusted by default, regardless of whether they operate within or outside the network perimeter. The model demands strict identity verification, continuous monitoring, and limited access to resources based on context.
CNAPPs are well positioned to support Zero Trust principles by enforcing least-privileged access and continuously monitoring cloud workloads and APIs for anomalous behavior. With components like cloud infrastructure entitlement management (CIEM) integrated, CNAPPs ensure that identities and permissions are tightly controlled, reducing the risk of overpermissioned accounts. Additionally, CNAPPs can detect lateral movement within cloud environments, blocking unauthorized access to sensitive resources.
The ability of CNAPPs to operate across multicloud and hybrid environments also complements the Zero Trust approach, ensuring consistent enforcement of policies no matter where workloads or users reside. As Zero Trust continues to shape the future of cybersecurity, CNAPPs will play an essential role in embedding these principles into cloud-native security strategies.
Cloud-Native Security FAQs
The market definition of CNAPP, as defined in Gartner’s 2024 Market Guide for Cloud-Native Application Protection Platforms is:
"Cloud-native application protection platforms (CNAPPs) are a unified and tightly integrated set of security and compliance capabilities designed to protect cloud-native infrastructure and applications. CNAPPs incorporate an integrated set of proactive and reactive security capabilities, including artifact scanning, security guardrails, configuration and compliance management, risk detection and prioritization, and behavioral analytics, providing visibility, governance and control from code creation to production runtime. CNAPP solutions use a combination of API integrations with leading cloud platform providers, continuous integration/continuous development (CI/CD) pipeline integrations, and agent and agentless workload integration to offer combined development and runtime security coverage."
Managed security service providers (MSSPs) specialize in delivering comprehensive security services, including threat monitoring, incident response, and compliance management. They offer expertise in securing various environments, including on-premises, hybrid, and multicloud infrastructures.
Cloud service providers, like AWS, Azure, and Google Cloud, offer cloud computing services, including storage, compute, and network resources. While CSPs provide some native security tools, their primary focus is on cloud infrastructure. MSSPs enhance security by integrating advanced tools and providing continuous security monitoring and management, often across multiple CSP platforms.
Managed service providers (MSPs) offer a broad range of IT services, including network management, system administration, and technical support. CSPs deliver cloud infrastructure services like compute, storage, and networking. MSSPs focus specifically on security services, such as threat detection, incident response, and compliance management.
Cloud managed service providers (CMSPs) combine the roles of MSPs and CSPs, managing cloud infrastructure and services while also ensuring optimized performance and cost-efficiency. Each provider type addresses distinct needs, from general IT support to specialized security and cloud management.