- What Is Application Security Posture Management (ASPM)?
-
State of ASPM 2026: Key Trends & Emerging Threats
- ASPM Market Evolution and Adoption Trajectory
- AI-Native ASPM and Machine Learning Integration
- Cloud-Native Security Challenges and Container Orchestration Threats
- Software Supply Chain Vulnerabilities and SBOM Evolution
- DevSecOps Integration and Future ASPM Architecture
- ASPM Key Trends & Threats FAQs
- How DSPM Is Evolving: Key Trends to Watch
- Top Cloud Data Security Solutions
- Interactive Application Testing & ASPM: Closing DevSec Gaps
- Buy or Build: Calculating ASPM ROI for Your Organization
- Overcoming AppSec Chaos: 7 Modes of ASPM Adoption
- ASPM: The Evolution Beyond ASOC
- Selecting Your ASPM Solution: Metrics That Matter
- ASPM in Action: 8 Real‑World Use Cases
-
Application Security Best Practices You Can’t Skip in ASPM
- ASPM Architecture: From Tool Sprawl to Unified Intelligence
- Advanced Risk Correlation and Contextual Prioritization Systems
- Policy-Driven Security Automation and Enforcement Architecture
- Seamless DevOps Integration and Cloud-Native Security Orchestration
- Enterprise Scalability, Performance Engineering, and Compliance Automation
- Application Security In ASPM Best Practices FAQs
-
How Supply Chain Threats Are Shaping ASPM Today
- The Supply Chain Attack Surface in Modern ASPM
- Critical Supply Chain Vectors Driving ASPM Evolution
- Software Supply Chain Risk Assessment and Prioritization
- Architectural Shifts in ASPM for Supply Chain Defense
- Operationalizing Supply Chain Security Within ASPM Programs
- Supply Chain Threats Are Shaping ASPM FAQs
-
How ASPM Strengthens Your Cloud Ecosystem
- ASPM's Role in Unified Cloud Security Architecture
- Integration Points Across the Cloud Security Stack
- Risk Intelligence and Contextual Prioritization in Cloud Environments
- Operational Efficiency Through Automated Cloud Security Workflows
- Strategic Advantages for Cloud-First Organizations
- ASPM Strengthening the Entire Cloud Ecosystem FAQs
-
Developer Infrastructure Posture: Integrating ASPM Early
- Understanding Developer Infrastructure Posture
- ASPM Fundamentals: Beyond Traditional Application Security
- Early Integration Strategies: Embedding ASPM in Developer Workflows
- ASPM Compliance Framework Integration
- Risk Prioritization and Remediation at Scale
- Developer Infrastructure Posture Management and ASPM FAQs
- Amplify ASPM with RBVM Risk‑Based Vulnerability Management
- CNAPP and ASPM Collaboration, Not Collision
- CSPM Vs ASPM: Where Your Focus Belongs
-
Why You Need Static Analysis, Dynamic Analysis, and Machine Learning?
-
What Is a Software Bill of Materials (SBOM)?
- Software Bill of Materials Explained
- Who Should Have a SBOM
- The Role of SBOMs in Cybersecurity and Compliance
- Why Is an SBOM Important?
- Software Composition Analysis and SBOMs
- How Does an SBOM Help Prevent Open-Source Supply Chain Attacks
- SBOM Formats
- Software Bill of Materials Best Practices
- SBOM FAQs
- What Is Policy-as-Code?
- What Is Static Application Security Testing (SAST)?
- What Is Software Composition Analysis (SCA)?
- What is Infrastructure-as-Code Security
- What is IaC?
- What Is Secrets Management?
- What Is Infrastructure as Code (IaC) Supply Chain Security?
- ASPM Tools: Evaluation Criteria and How to Select the Best Option
What Is Code Security?
Code security refers to embedding security into code. Unlike traditional cloud security posture management and cloud workload protection solutions, cloud code security focuses on code with several use cases, including infrastructure as code (IaC) security, application code security and software supply chain security.
Cloud-native technologies, such as IaC and containers, combine application and infrastructure development principles, allowing for greater flexibility, scalability and usability. These technologies have not only changed the way we build the cloud but also how we secure it.
IaC Security
Infrastructure as code is a modern technology and process in which infrastructure is provisioned and managed using machine-readable code files. Frameworks such as Terraform and CloudFormation allow teams to write declarative or imperative code files, check those files into their version control system and CI/CD pipeline, and then spin up the cloud resources across environments.
IaC introduces new security considerations that traditional approaches to security don’t address. Traditional security typically monitors for cloud security issues, also known as misconfigurations, in runtime environments. With IaC, one misconfiguration in a code file can lead to thousands of misconfigurations and alerts across cloud environments.
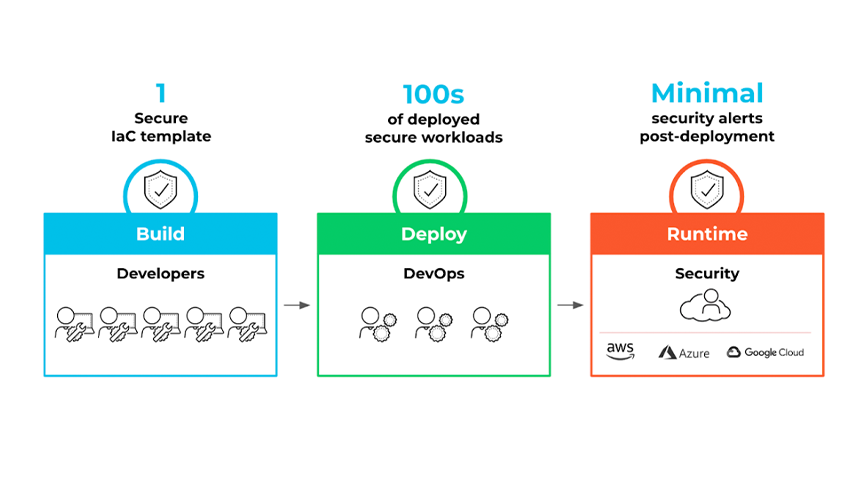
Figure 1: A secure IaC template through to deploy and runtime phases of the development lifecycle
Code security solves this by surfacing security feedback earlier in the development lifecycle instead of taking a reactive approach. Addressing misconfigurations during the development and build phases allows for faster and cheaper remediations – before deployment. This reduces noisy alerts that security teams have to triage and cuts down on the time engineering spends addressing issues ad hoc.
The key to a successful code security strategy for IaC is ensuring security is embedded directly in developer tools and workflows. By surfacing actionable feedback in code and embedding security guardrails in the build pipeline, IaC security empowers developers to ship infrastructure that’s secure by default.
Application Code Security
Code security for applications focuses on identifying known vulnerabilities in source code, dependencies and open source packages. Vulnerabilities, specifically Common Vulnerabilities and Exposures (CVEs), can introduce security risks across an application’s development stages, but code security focuses on the application code itself.
A strong code security strategy relies on secure coding best practices and code reviews to identify vulnerabilities. Through automated testing with technologies such as static application security testing (SAST) for custom code and software composition analysis (SCA) for open source code, code security solutions complement cloud workload protection by identifying CVEs as early as possible.
Again, the key to a strong code security strategy for applications is to provide actionable vulnerability findings to the people with the most context and knowledge about the code: developers. This is achieved through developer integrations and granular controls for how compliant versions can be bumped.
The other key to a cohesive code security strategy is context and visibility between infrastructure misconfigurations and application vulnerabilities. The lines between infrastructure and applications are blurred within cloud-native applications. Infrastructure is the foundation on which applications run and thus are inextricably linked. The same goes for security.
Having visibility into both the infrastructure and application layers of cloud-native applications improves teams’ ability to prioritize and address security issues based on their real-world exploitability. Improved visibility also enables teams to more quickly patch identified vulnerabilities, revoke overly permissive access, and lock down the relevant virtual machines (VMs) to minimize an attack’s blast radius.
Software Supply Chain Security
Software supply chains comprise application and infrastructure components as well as the underlying pipelines, including version control systems (VCS), continuous integration and continuous deployment (CI/CD) pipelines, and registries. And a cloud-native application is only as secure as its weakest link. So that’s why securing those delivery pipelines is also an essential part of code security.
If a VCS isn’t securely configured, attackers may be able to merge malicious code or get access to exposed secrets that could lead to a larger attack. And if CI/CD pipelines are compromised, attackers can gain access to exposed credentials and tamper with code, which can result in downstream incidents. Supply chain security best practices focus on hardening pipelines and configuring access controls and branch protections to restrict access as much as possible.
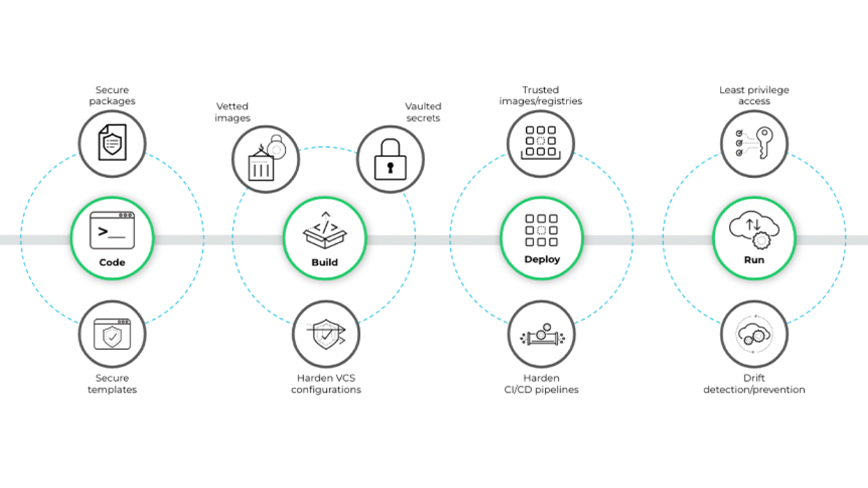
Figure 2: Secure components and pipelines within a software supply chain
Software supply chain security is an important part of a strong code security strategy, as is understanding the connections between pipelines and infrastructure and application code across the development lifecycle. By increasing visibility across software supply chains, code security solutions enable teams to fully take advantage of all the benefits of cloud-native technologies and secure their infrastructure from code to cloud.