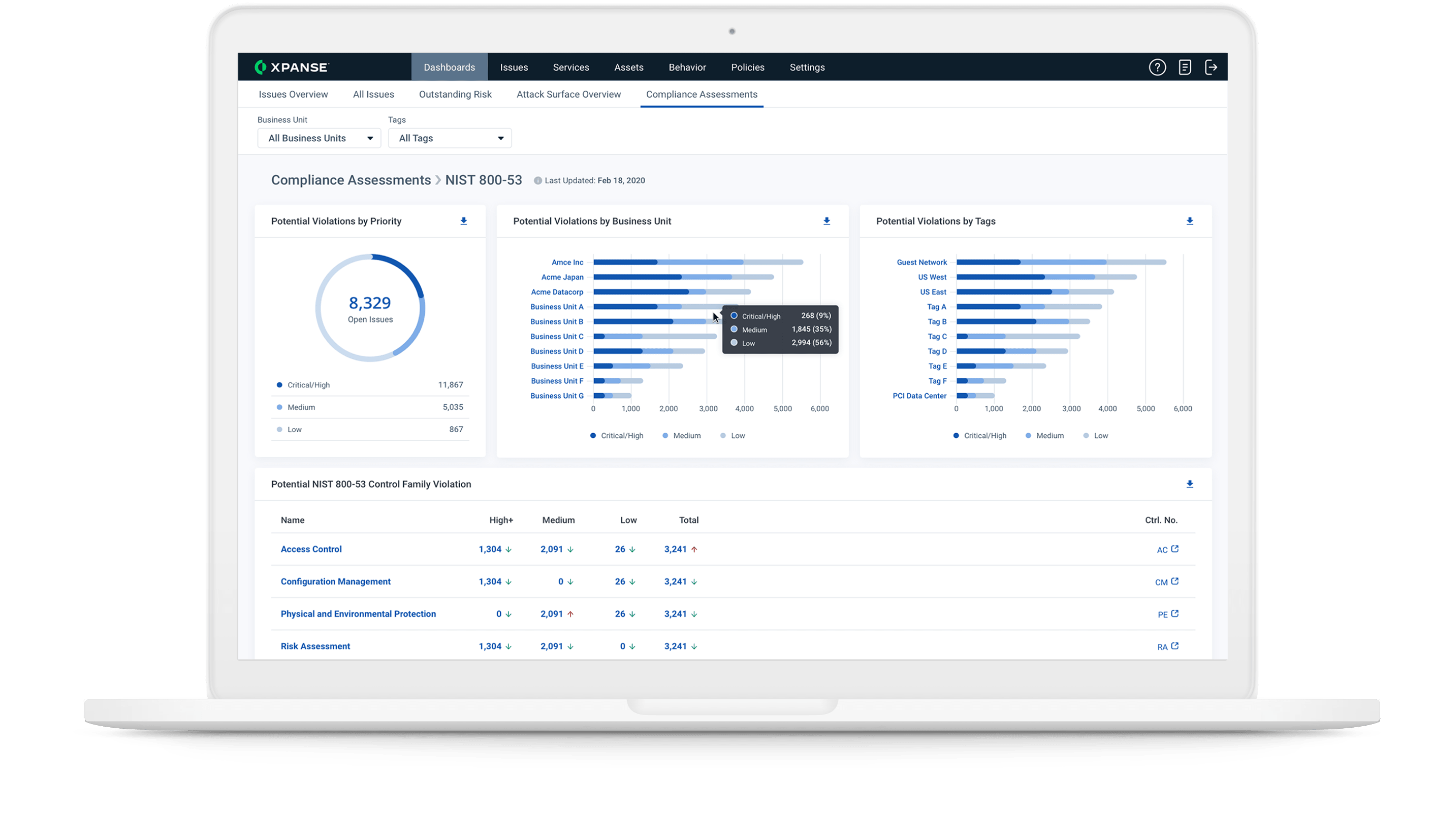
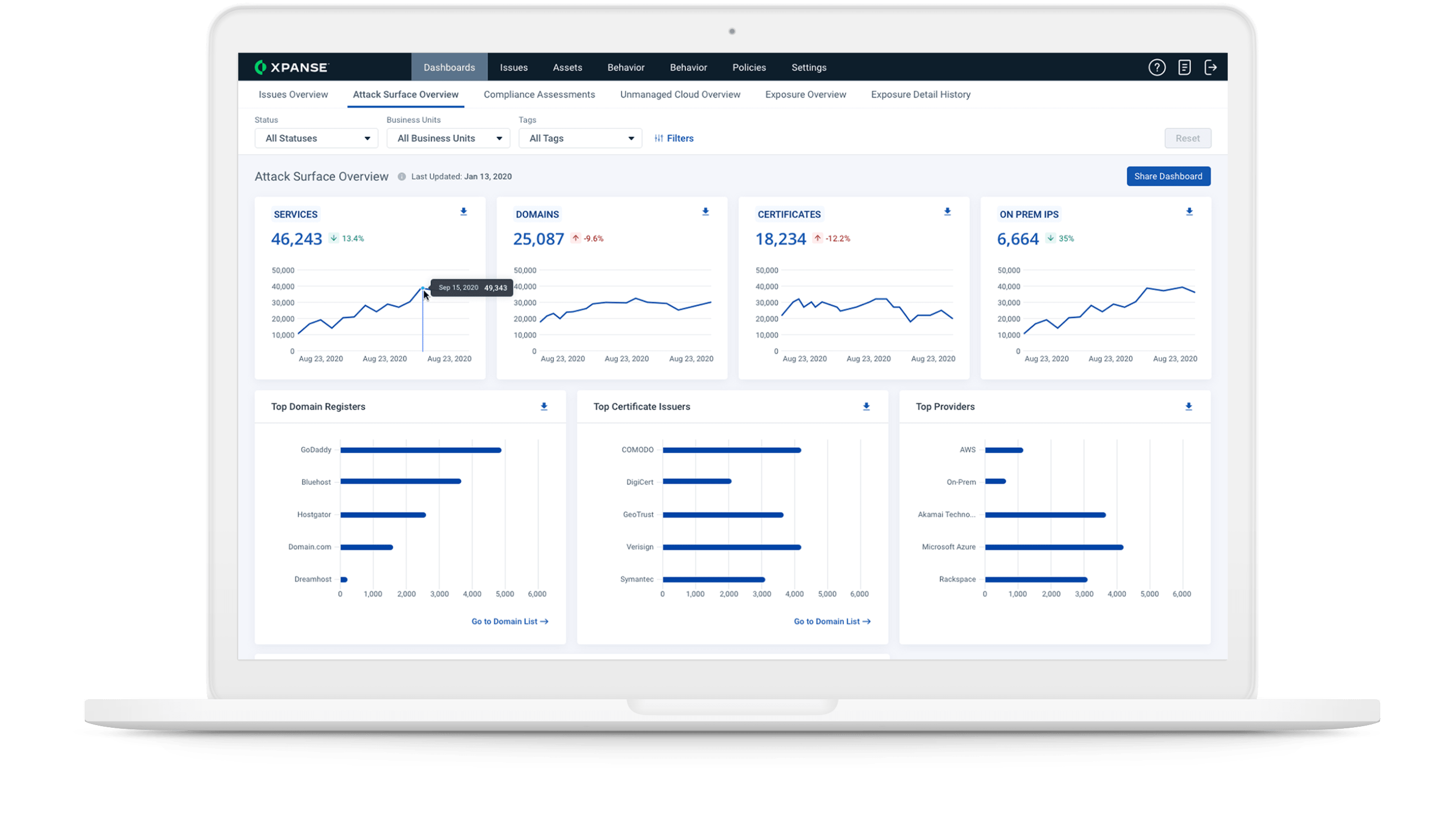
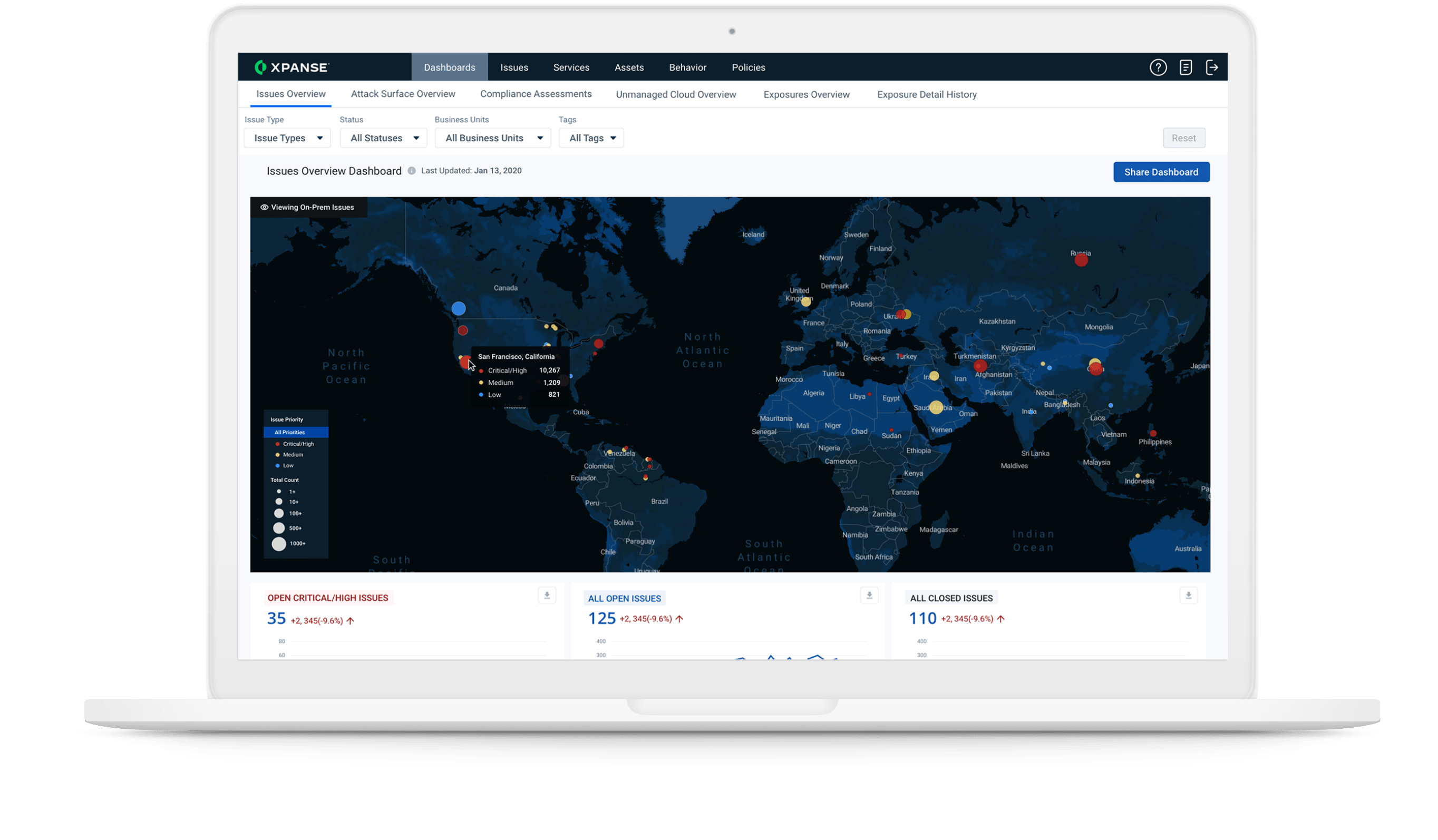
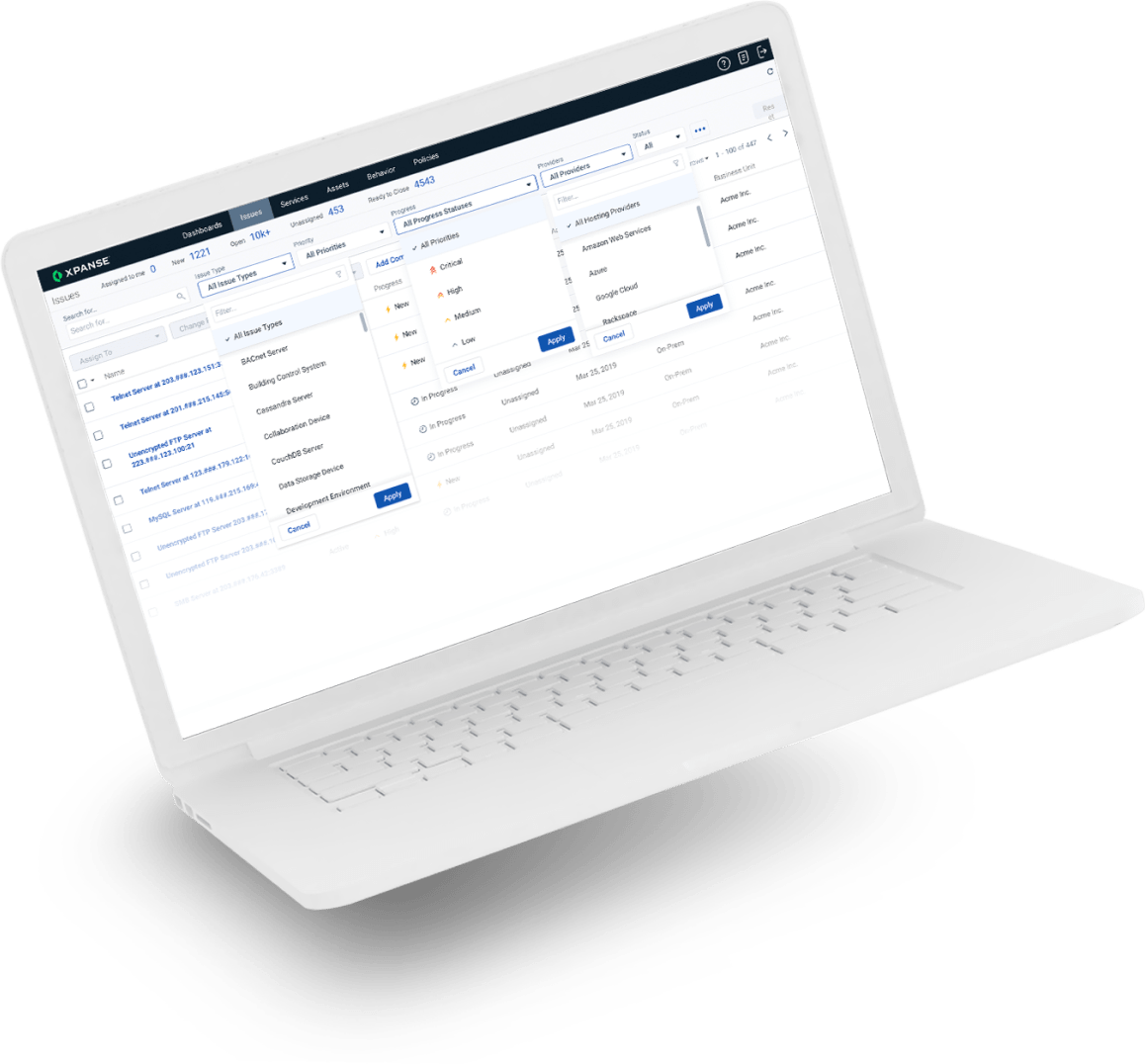
An attacker view of your attack surface
Internal scans are only as effective as the assets inventory they review. Scanning from the outside-in ensures a complete view of all internet-connected assets that pose a risk to your organization, especially if they belong to someone else.
Don’t inherit risk through M&A
Just as Xpanse can build a record of your assets, it can do the same for an acquired company.
Discover third-party exposures
Xpanse Link finds the internet-connected assets owned by third-party vendors or supply chain partners that could put your organization at risk.